Turns out, a new Java vulnerability is being exploited in the wild as I speak, with exploits already being put to use across some of the most popular crimeware toolkits. So where does it exist? ALL VERSIONS OF JAVA 7!
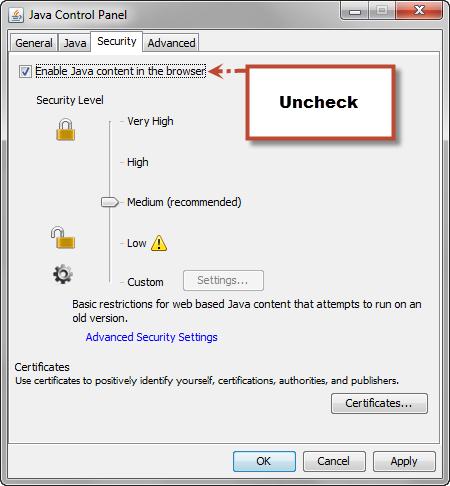
While Oracle took the rare step of releasing an out-of-band patch for that zero-day bug a few days after the flaw was identified, at the moment, there is no word of a fix or mitigation controls from the company at this time. Users should disable the Java plugin (version 1.7) in their browser (or if they already have done so, leave it disabled for the time being).
Full story can be found here.
(Source: SecurityWeek)
Page 1 / 2
Hi,
Long time user first time poster. We are utilizing webroot for our remote users. I have a quick question:
1. Will webroot protect against this?
2. I have read this exploit uses a mechanism to elevate privileges. So (webroot aside) are standard users without administrative rights still vulnerable?
Thanks...
Long time user first time poster. We are utilizing webroot for our remote users. I have a quick question:
1. Will webroot protect against this?
2. I have read this exploit uses a mechanism to elevate privileges. So (webroot aside) are standard users without administrative rights still vulnerable?
Thanks...
Hello kcsteele and Welcome to the Webroot Community Forums.
WSA doesn't do anything to protect from the Exploit as it's a hole in Java itself but if it does to try to drop and run malware that's when WSA would come into play and Block the malware from running and it would ask you to do a scan that would remove the dropper.
HTH,
TH
WSA doesn't do anything to protect from the Exploit as it's a hole in Java itself but if it does to try to drop and run malware that's when WSA would come into play and Block the malware from running and it would ask you to do a scan that would remove the dropper.
HTH,
TH
Thanks TripleHelix. Would you happen to know if non-admin users are vulnerable? I have found nowhere that explicitly states this, and strangely the MS-ISAC advisory indicates "running as non privileged user will dimish the effects of the attack", however I think that is just set in the notification template they use.
Yes that could help for Vista or Win 7 & 8 with UAC to the Max in a limited user account but many articles I read says that it drops a malware EXE file so it would have execute to do anything and WSA would see the dropper being written to the drive and Block it. Read the article that Yegor posted to learn more.
TH
TH
Thanks, I read the article and I have read a few others as well, but none seem to directly address whether non-privileged users are as vulnerable as privileged ones. I also have seen proof of concept working exploits however none of those identify whether the user context was privileged or not.
Typically in the case of non-privileged users not being vulnerable they will state it. However I have not seen this so I guess we'll have to assume they are.
Typically in the case of non-privileged users not being vulnerable they will state it. However I have not seen this so I guess we'll have to assume they are.
Well the reason I'm asking is not for myself but because most of our users here are non-privileged and run IE (not by my choice), I might be facing having to go around and do this for all of them or at least find some way of centrally configuring it.
Well this is where WSA will protect you with it's Anti-Malware, Firewall, Identity Shield and Journaling if it's unknown. I'm not sure if you seen this Video?
TH
TH
Thanks, currently we are running the cloud based webroot site filtering and traffic inspection service only for our remote users. On our LAN we have all the typical security measures but not webroot. You said at this point there is no proactive protection and webroot would only retroactively attempt to remove the infection. So I am more concerned with finding out how necessary it is to disable java in the browser for non privileged users. Thanks again.
Have you ever thought of giving SecureAnywhere Business - Endpoint Protection a Trial Run? http://www.webroot.com/En_US/business/secureanywhere-endpoint/
TH
TH
I dont handle that stuff here just the admin but I'll pass it on.
Thanks again.
Thanks again.
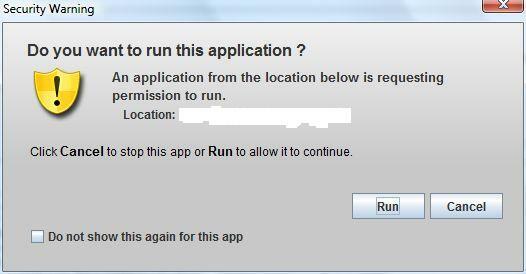
Yeah, Java is a pain as far as security. Unfortunately Java is spread over many platforms and you can't avoid it completly unless you resign on web applications they are using it. However it's not sometimes possible. Java is used by many bank houses for their online banking applications what is also the case of mine. Therefore if you can't disable Java like me I recomend to elevate the security level to High at least. It will trigger a prompt every time an application is requesting permission to run (see below picture).
It's me again :D
In relation to the latest Java vulnerability I am curious to learn if using sanboxed IE9 in SafeStart Sandbox under System Tools, click System Control, and click Start is wise and recommended. As I said in my previous post I can't give up on Java because of my online banking system. However I want to tighten my security as much as possible. Though I am not sure if it is workable solution because in the user guide there is written "Note: The SafeStart Sandbox is intended for testing malware, not legitimate programs" and moreover I don't know whether sanboxed IE9 will load with plugins which are necessary for my banking (Java and Flash). Furthermore I don't know if sanboxed IE9 will be more bulletproof against the said Java vulnerability.
Can you shed more light?
BTW, I use Opera as a prime browser. However the latest Oracle Java plugins don't work in Opera 32-bit, so I have to use IE9 instead for my banking.
In relation to the latest Java vulnerability I am curious to learn if using sanboxed IE9 in SafeStart Sandbox under System Tools, click System Control, and click Start is wise and recommended. As I said in my previous post I can't give up on Java because of my online banking system. However I want to tighten my security as much as possible. Though I am not sure if it is workable solution because in the user guide there is written "Note: The SafeStart Sandbox is intended for testing malware, not legitimate programs" and moreover I don't know whether sanboxed IE9 will load with plugins which are necessary for my banking (Java and Flash). Furthermore I don't know if sanboxed IE9 will be more bulletproof against the said Java vulnerability.
Can you shed more light?
BTW, I use Opera as a prime browser. However the latest Oracle Java plugins don't work in Opera 32-bit, so I have to use IE9 instead for my banking.
It works for me in Opera I use Java SE Runtime Environment 7u10. I just run a Internet speed test http://speedtest.sourcecable.ca/@ wrote:
BTW, I use Opera as a prime browser. However the latest Oracle Java plugins don't work in Opera 32-bit, so I have to use IE9 instead for my banking.
TH
Thanks TH for the feedback. Yes because you use 64-bit, don't you?@ wrote:
It works for me in Opera I use Java SE Runtime Environment 7u10.@ wrote:
BTW, I use Opera as a prime browser. However the latest Oracle Java plugins don't work in Opera 32-bit, so I have to use IE9 instead for my banking.
TH
I rather uninstalled update 10 in the security sake and installed update 9 that also works in Opera (BTW, since update 10 Oracle uses different way to deploy Java plugins what makes the issue with Opera as talked yesterday).
Furthermore it looks like that my yesterday's post fell in rush so I take opportunity to post it again below.
In relation to the latest Java vulnerability I am curious if using sanboxed IE9 in SafeStart Sandbox under System Tools, click System Control, and click Start is wise and recommended. As I said in my previous post I can't give up on Java because of my online banking system. However I want to tighten my security as much as possible. Though I am not sure if it is workable solution because in the user guide there is written "Note: The SafeStart Sandbox is intended for testing malware, not legitimate programs" and moreover I don't know whether sanboxed IE9 will load with plugins which are necessary for my banking (Java and Flash).
Last but not least will sanboxed IE9 be more bulletproof against the said Java vulnerability? I mean IE9 is Protected by the Identity Shiled, so does it have sence to sandbox IE?
Furthermore it looks like that my yesterday's post fell in rush so I take opportunity to post it again below.
In relation to the latest Java vulnerability I am curious if using sanboxed IE9 in SafeStart Sandbox under System Tools, click System Control, and click Start is wise and recommended. As I said in my previous post I can't give up on Java because of my online banking system. However I want to tighten my security as much as possible. Though I am not sure if it is workable solution because in the user guide there is written "Note: The SafeStart Sandbox is intended for testing malware, not legitimate programs" and moreover I don't know whether sanboxed IE9 will load with plugins which are necessary for my banking (Java and Flash).
Last but not least will sanboxed IE9 be more bulletproof against the said Java vulnerability? I mean IE9 is Protected by the Identity Shiled, so does it have sence to sandbox IE?
To me doing your banking would be fine it's when you visit other sites that have been compromised which would try to download the payload I only use it to do my Internet Speed Test as it records them on DSLR to compare against others with my ISP http://www.dslreports.com/archive/rogers.com?zip=&cid=&p=2 other wise I don't need it but never had a problem either in the past!
TH
TH
Java 7 fails to restrict access to privileged code
Original Release date: 10 Jan 2013 | Last revised: 12 Jan 2013
Overview
Java 7 Update 10 and earlier Java 7 versions contain an unspecified vulnerability that can allow a remote, unauthenticated attacker to execute arbitrary code on a vulnerable system.
Impact
By convincing a user to visit a specially crafted HTML document, a remote attacker may be able to execute arbitrary code on a vulnerable system. Note that applications that use the Internet Explorer web content rendering components, such as Microsoft Office or Windows Desktop Search, may also be used as an attack vector for this vulnerability.
http://www.kb.cert.org/vuls/id/625617
This is where WSA would step in!
TH
Original Release date: 10 Jan 2013 | Last revised: 12 Jan 2013
Overview
Java 7 Update 10 and earlier Java 7 versions contain an unspecified vulnerability that can allow a remote, unauthenticated attacker to execute arbitrary code on a vulnerable system.
Impact
By convincing a user to visit a specially crafted HTML document, a remote attacker may be able to execute arbitrary code on a vulnerable system. Note that applications that use the Internet Explorer web content rendering components, such as Microsoft Office or Windows Desktop Search, may also be used as an attack vector for this vulnerability.
http://www.kb.cert.org/vuls/id/625617
This is where WSA would step in!
TH
Page 1 / 2
Reply
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.