Lately, our resources page has been filling up with some fascinating material about all of our Webroot solutions.
Quite a few insightful and illuminating papers have recently been posted concerning our anti-virus endpoint protection, our mobile protection, and our web security protection. Just to name a few...
1. User-Based Licensing for Endpoint Protection and BYOD
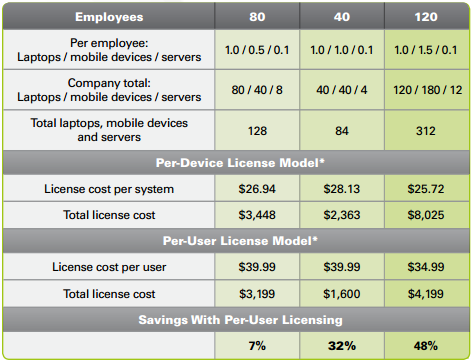
What happens when you license by device? You get more devices, you end up paying more money and giving yourself an administrative headache in the process. What happens when you license by user? It's easier to administrate, easier to budget, and you save yourself some money in the process. These reasons and others are covered in this thought-provoking whitepaper. This graphic and others can be found within:
Look at that savings!
2. Closing the Circle
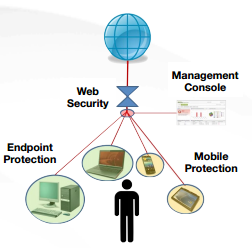
Do you have Endpoint security but not Mobile security? Do you have Web Filtering but no Endpoint protection? Most employees have two, three, or four devices connected to the internet. They use those devices for work, but they also use them for play - and that means those devices are more exposed to malware. A common question we often hear is "Why do I need multiple kinds of protection?" The answer to that question is in this whitepaper, which explains our layered approach and how our three methods of protection all complement each other to provide an incredibly robust, effective, and user-friendly platform.
3. BYOD - The SMB Mobile Threat
Who doesn't love an infographic? Well, maybe malware authors in this case, since this one works against their interests by educating you about mobile device usage in your workplace. Did you know employee tablet use will see a year-to-year increase of 50%? Did you know that 79% of companies that don't support BYOD say their employees use personal mobile devices for business anyway? With as many as 10% of mobile applications containing either malicious or undesirable behavior and the prevalence of mobile devices in the workplace, the time has come to do something about it. Check out the infographic for more information. Here is a snippet:
4. Phishing 2.0
At one point, it seemed that phishing was receding to the status of a minor issue threatening only naïve consumers. But a new version has emerged, fueled by new cybercriminals and new phishing techniques. New types of phishing campaigns are particularly worrisome for businesses for a number of reasons. They are aimed at businesses (including small and midsize businesses) rather than consumers. They evade traditional antivirus and antiphishing products. They can fool even security-savvy computer users by using information gathered from social media and other web sources. And they often target employees ith access to the most sensitive information, such as bank accounts, customer lists and intellectual property. So how do these phising attacks work, and how does Webroot stop them? Please take a look at the whitepaper to learn more.
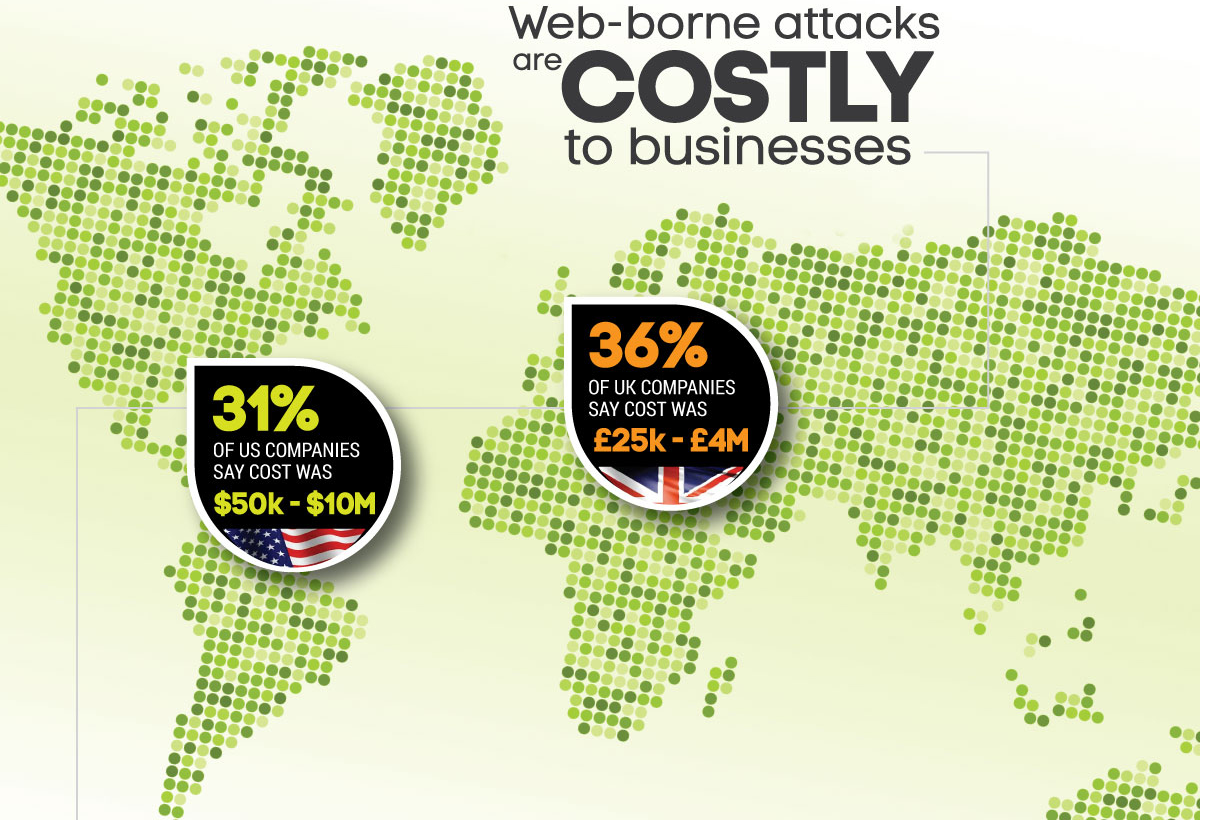
5. Web Security Infographic
This infographic snippet pretty much speaks for itself in terms of dollars lost (or pounds as the case may be). But if you're not convinced you need the most powerful web security available, take a look at the linked infographic for even more mindblowing information about threats, data breaches, and hacks.
If you have questions or comments on any of these whitepapers and infographics, please feel free to reply and let us know. We'll be happy to field your questions.
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.