June 16th, 2014, 15:46 GMT · By Ionut Ilascu
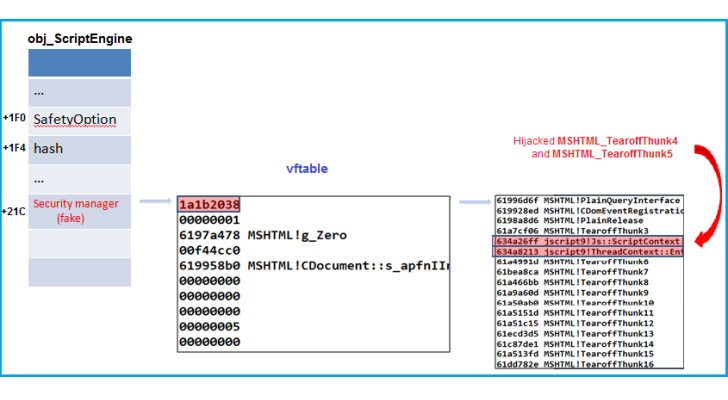
Script engine object modified by Yuki Chen's ExpLib2
Exploit mitigation techniques available in Internet Explorer keep the browser strong in face of memory exploits, but attacks could be carried out through the script interpreter engine.
In a blog post from network security firm Fortinet security researcher Zhenhua Liu explains how exploit researchers may have opened the box of Pandora as far as the safety of Microsoft’ browser is concerned.
He shows that scripts can be as efficient as a shellcode and that malicious scripts can be run by script interpreter engine on a target machine with escalated privileges, based on the discoveries of Yang Yu (CanSecWest 2014 presentation), Yuki Chen and Yuange (Chinese).
Liu says that “the safety of the IE script engine relies solely on one single byte - the SafetyOption flag.” Getting elevated privileges requires modifying the flag to 0 (zero) or in JScript and 0 (zero) in VBScript. Full Article
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.