by Dennis Fisher July 16, 2014
Although the average size of a given DDoS attack is going down, the number of attacks at the upper end of the scale is increasing, with researchers at Arbor Networks reporting more than 100 attacks of 100 Gbps in the first half of this year.
In order for a DDoS attack to be effective, bad guys used to need hundreds or even thousands of compromised machines to throw relatively large amounts of traffic at a target. But now, with high-bandwidth connections available to many home Internet users, attackers can generate huge traffic volumes with a much smaller number of bots and can completely overwhelm many targets. Arbor’s research shows that the number of DDoS attacks that peak at high traffic volumes of more than 100 Gbps is continuing to grow.
Read the story
Userlevel 7
The following article is a update on DDOS Attacks
(Average Peak Size of DDoS Attacks Spiked in Q2: VeriSign)
By Eduard Kovacs on August 17, 2014
The average peak size of distributed denial-of-service (DDoS) attacks in the second quarter of 2014 increased by 216% compared to the first quarter, according to the latest trends report from VeriSign.
The report shows a year-on-year increase of 291% in average peak attack size, with 65% of the cyberattacks monitored by the company exceeding 1 Gbps. This is worrying news, especially for small and medium size businesses that usually have less than 1 Gbps of upstream bandwidth. Between April 1 and June 30, attacks in the 5-10 Gbps range increased by 33%, while ones greater than 10 Gbps increased by 16% compared to the first three months of 2014.
The media and entertainment industry has been the most targeted (43%), followed closely by the IT services/SaaS/cloud sector (41%). The financial and the public sectors each accounted for only 5% of attacks, the company noted.
SecurityWeek/ full article here/ http://www.securityweek.com/average-peak-size-ddos-attacks-spiked-q2-verisign
(Average Peak Size of DDoS Attacks Spiked in Q2: VeriSign)
By Eduard Kovacs on August 17, 2014
The average peak size of distributed denial-of-service (DDoS) attacks in the second quarter of 2014 increased by 216% compared to the first quarter, according to the latest trends report from VeriSign.
The report shows a year-on-year increase of 291% in average peak attack size, with 65% of the cyberattacks monitored by the company exceeding 1 Gbps. This is worrying news, especially for small and medium size businesses that usually have less than 1 Gbps of upstream bandwidth. Between April 1 and June 30, attacks in the 5-10 Gbps range increased by 33%, while ones greater than 10 Gbps increased by 16% compared to the first three months of 2014.
The media and entertainment industry has been the most targeted (43%), followed closely by the IT services/SaaS/cloud sector (41%). The financial and the public sectors each accounted for only 5% of attacks, the company noted.
SecurityWeek/ full article here/ http://www.securityweek.com/average-peak-size-ddos-attacks-spiked-q2-verisign
Userlevel 7
The following article is a update on DDOS Attacks
(High-volume DDoS attacks on the rise)
By HNS Staff/ Posted on 23 September 2014.
Attacks continue to be short in duration with repeated frequency:More than 90 percent of attacks detected lasted less than 30 minutes. This ongoing trend indicates that latency-sensitive websites, such as online gaming, eCommerce and hosting service should be prepared toimplement security solutions that support rapid response.
High-rate, high-volume attacks increased: DDoS traffic volume was up overall with a third peaking at over 500Mbps and more than five percent reaching up to 4Gbps. In addition, findings showed that over 50% DDoS attacks were above 0.2Mpps in the first half of 2014, increasing from around 16%. And over 2% of DDoS attacks were launched at a rate of over 3.2Mpps.
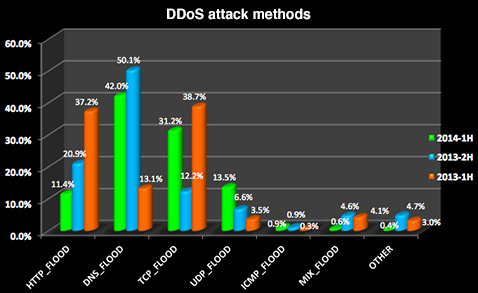
Top three DDoS attack methods revealed: HTTP Flood, TCP Flood and DNS Flood were the top three attack types, together making up 84.6 percent of all attacks. DNS Flood attacks held their place as the most popular attack method, accounting for 42 percent of all attacks. While the number of DNS and HTTP Flood attacks decreased, TCP Flood attacks grew substantially.
Increase in ISPs, enterprises and online gaming targets: Attacks targeting ISPs increased by 87.2 percent, enterprises by 100.5 percent and online gaming by 60 percent.
Longest, largest and highest-frequency attacks: The longest single attack lasted nine days and 11 hours, or 228 hours, while the single largest attack in terms of packet-per-second (pps) hit at a volume of 23 million pps. More than 42 percent of attack victims were targeted multiple times while one in every 40 victims was repeatedly hit more than 10 times. The highest frequency of attacks experienced by a single victim was 68 separate DDoS attacks.
Help Net Security/full article here/ http://www.net-security.org/secworld.php?id=17398
(High-volume DDoS attacks on the rise)
By HNS Staff/ Posted on 23 September 2014.
Attacks continue to be short in duration with repeated frequency:More than 90 percent of attacks detected lasted less than 30 minutes. This ongoing trend indicates that latency-sensitive websites, such as online gaming, eCommerce and hosting service should be prepared toimplement security solutions that support rapid response.
High-rate, high-volume attacks increased: DDoS traffic volume was up overall with a third peaking at over 500Mbps and more than five percent reaching up to 4Gbps. In addition, findings showed that over 50% DDoS attacks were above 0.2Mpps in the first half of 2014, increasing from around 16%. And over 2% of DDoS attacks were launched at a rate of over 3.2Mpps.
Top three DDoS attack methods revealed: HTTP Flood, TCP Flood and DNS Flood were the top three attack types, together making up 84.6 percent of all attacks. DNS Flood attacks held their place as the most popular attack method, accounting for 42 percent of all attacks. While the number of DNS and HTTP Flood attacks decreased, TCP Flood attacks grew substantially.
Increase in ISPs, enterprises and online gaming targets: Attacks targeting ISPs increased by 87.2 percent, enterprises by 100.5 percent and online gaming by 60 percent.
Longest, largest and highest-frequency attacks: The longest single attack lasted nine days and 11 hours, or 228 hours, while the single largest attack in terms of packet-per-second (pps) hit at a volume of 23 million pps. More than 42 percent of attack victims were targeted multiple times while one in every 40 victims was repeatedly hit more than 10 times. The highest frequency of attacks experienced by a single victim was 68 separate DDoS attacks.
Help Net Security/full article here/ http://www.net-security.org/secworld.php?id=17398
Userlevel 7
The following article is a update
************************************
By Ian Barker
A total of 23,095 DDoS attacks were carried out on web resources located in 76 countries in the first quarter of 2015, up 15 percent from the 66 countries affected in the final quarter of last year.
This is one of the findings of a new study by cyber security firm Kaspersky Lab into the botnet-assisted DDoS attack landscape. But although the geography is expanding the overall number of botnet-assisted attacks is down by 11 percent and the number of unique victims down by eight percent.
Servers in the US, Canada and China are targeted most frequently. The study also finds that the greatest number of attacks on a single web resource in Q1 2015 was 21, compared to 16 in Q4 2014, and the most prolonged botnet attack occurred for almost six days.
"A DDoS attack is often a cross-border effort; the customer is located in one country, the executor in another, the C&C servers are hosted in a third country, and the bots involved in the DDoS attack are scattered across the world," says Evgeny Vigovsky, Head of DDoS Protection at Kaspersky Lab. "This often makes it more complicated to investigate attacks, take down botnets and catch those responsible. Although cybercriminals do not limit their DDoS toolkits to botnets alone, this is still a widespread and dangerous tool, and it demands preventive protection measures from potential targets, i.e. web resources".
full article
************************************
By Ian Barker
A total of 23,095 DDoS attacks were carried out on web resources located in 76 countries in the first quarter of 2015, up 15 percent from the 66 countries affected in the final quarter of last year.
This is one of the findings of a new study by cyber security firm Kaspersky Lab into the botnet-assisted DDoS attack landscape. But although the geography is expanding the overall number of botnet-assisted attacks is down by 11 percent and the number of unique victims down by eight percent.
Servers in the US, Canada and China are targeted most frequently. The study also finds that the greatest number of attacks on a single web resource in Q1 2015 was 21, compared to 16 in Q4 2014, and the most prolonged botnet attack occurred for almost six days.
"A DDoS attack is often a cross-border effort; the customer is located in one country, the executor in another, the C&C servers are hosted in a third country, and the bots involved in the DDoS attack are scattered across the world," says Evgeny Vigovsky, Head of DDoS Protection at Kaspersky Lab. "This often makes it more complicated to investigate attacks, take down botnets and catch those responsible. Although cybercriminals do not limit their DDoS toolkits to botnets alone, this is still a widespread and dangerous tool, and it demands preventive protection measures from potential targets, i.e. web resources".
full article
Reply
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.