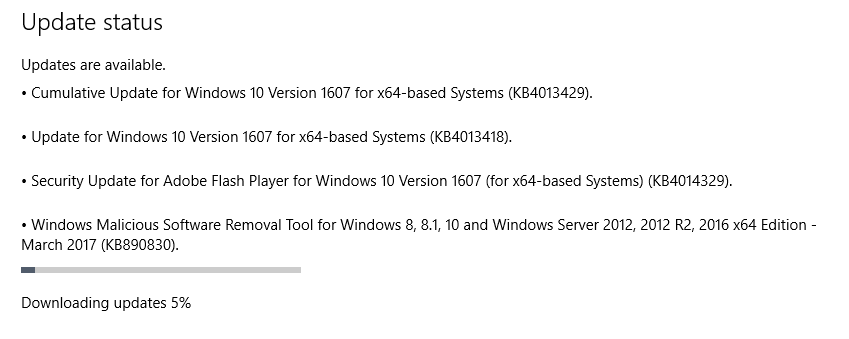
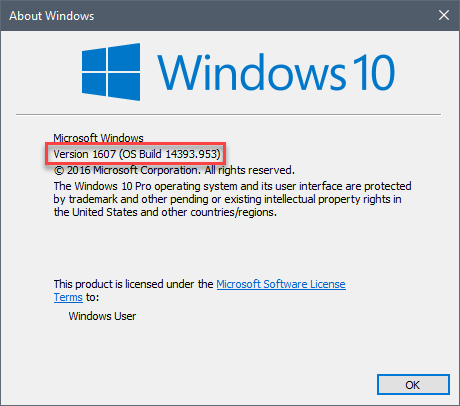
So far on Windows 10. I or others will post more when info becomes available!
March 2017 security update release
https://blogs.technet.microsoft.com/msrc/2017/03/14/march-2017-security-update-release/
Microsoft Security Bulletin Summary for March 2017
Bulletin ID
Bulletin Title and Executive Summary
Maximum Severity Rating
and Vulnerability Impact
Restart Requirement
Known
Issues
Affected Software
MS17-006
Cumulative Security Update for Internet Explorer (4013073)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows,
Microsoft Internet Explorer
MS17-007
Cumulative Security Update for Microsoft Edge (4013071)
This security update resolves vulnerabilities in Microsoft Edge. These vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited these vulnerabilities could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows,
Microsoft Edge
MS17-008
Security Update for Windows Hyper-V (4013082)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an authenticated attacker on a guest operating system runs a specially crafted application that causes the Hyper-V host operating system to execute arbitrary code. Customers who have not enabled the Hyper-V role are not affected.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows
MS17-009
Security Update for Microsoft Windows PDF Library (4010319)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user views specially crafted PDF content online or opens a specially crafted PDF document.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows
MS17-010
Security Update for Microsoft Windows SMB Server (4013389)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an attacker sends specially crafted messages to a Microsoft Server Message Block 1.0 (SMBv1) server.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows
MS17-011
Security Update for Microsoft Uniscribe (4013076)
This security update resolves vulnerabilities in Windows Uniscribe. The most severe of these vulnerabilities could allow remote code execution if a user visits a specially crafted website or opens a specially crafted document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows
MS17-012
Security Update for Microsoft Windows (4013078)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an attacker runs a specially crafted application that connects to an iSNS Server and then issues malicious requests to the server.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows
MS17-013
Security Update for Microsoft Graphics Component (4013075)
This security update resolves vulnerabilities in Microsoft Windows, Microsoft Office, Skype for Business, Microsoft Lync, and Microsoft Silverlight. The most severe of these vulnerabilities could allow remote code execution if a user either visits a specially crafted website or opens a specially crafted document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows
Microsoft Office,
Skype for Business,
Microsoft Lync,
Microsoft Silverlight
MS17-014
Security Update for Microsoft Office (4013241)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
Important
Remote Code Execution
May require restart
---------
Microsoft Office,
Microsoft Office Services and Web Apps,
Microsoft Server Software,
Microsoft Communications Platforms and Software
MS17-015
Security Update for Microsoft Exchange Server (4013242)
This security update resolves a vulnerability in Microsoft Exchange Outlook Web Access (OWA). The vulnerability could allow remote code execution in Exchange Server if an attacker sends an email with a specially crafted attachment to a vulnerable Exchange server.
Important
Remote Code Execution
Requires restart
---------
Microsoft Exchange
MS17-016
Security Update for Windows IIS (4013074)
This security update resolves a vulnerability in Microsoft Internet Information Services (IIS). The vulnerability could allow elevation of privilege if a user clicks a specially crafted URL which is hosted by an affected Microsoft IIS server. An attacker who successfully exploited this vulnerability could potentially execute scripts in the user’s browser to obtain information from web sessions.
Important
Remote Code Execution
Requires restart
---------
Microsoft Windows
MS17-017
Security Update for Windows Kernel (4013081)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker runs a specially crafted application.
Important
Elevation of Privilege
Requires restart
---------
Microsoft Windows
MS17-018
Security Update for Windows Kernel-Mode Drivers (4013083)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system.
Important
Elevation of Privilege
Requires restart
---------
Microsoft Windows
MS17-019
Security Update for Active Directory Federation Services (4010320)
This security update resolves a vulnerability in Active Directory Federation Services (ADFS). The vulnerability could allow information disclosure if an attacker sends a specially crafted request to an ADFS server, allowing the attacker to read sensitive information about the target system.
Important
Information Disclosure
Requires restart
---------
Microsoft Windows
MS17-020
Security Update for Windows DVD Maker (3208223)
This security update resolves an information disclosure vulnerability in Windows DVD Maker. The vulnerability could allow an attacker to obtain information to further compromise a target system.
Important
Information Disclosure
Requires restart
---------
Microsoft Windows
MS17-021
Security Update for Windows DirectShow (4010318)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow an information disclosure if Windows DirectShow opens specially crafted media content that is hosted on a malicious website. An attacker who successfully exploited the vulnerability could obtain information to further compromise a target system.
Important
Information Disclosure
Requires restart
---------
Microsoft Windows
MS17-022
Security Update for Microsoft XML Core Services (4010321)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure if a user visits a malicious website. However, in all cases an attacker would have no way to force a user to click a specially crafted link. An attacker would have to convince a user to click the link, typically by way of an enticement in an email or Instant Messenger message.
Important
Information Disclosure
Requires restart
---------
Microsoft Windows
MS17-023
Security Update for Adobe Flash Player (4014329)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, Windows 10, and Windows Server 2016.
Critical
Remote Code Execution
Requires restart
---------
Microsoft Windows,
Adobe Flash Player
https://technet.microsoft.com/en-us/library/security/ms17-mar
Improvements and fixes
This update includes quality improvements. No new operating system features are being introduced in this update. Key changes include:
If you installed earlier updates, only the new fixes contained in this package will be downloaded and installed on your device.
Known issues in this update
Microsoft is not currently aware of any issues with this update.
How to get this update
This update will be downloaded and installed automatically from Windows Update. To get the stand-alone package for this update, go to the Microsoft Update Catalog website.
Download KB4013429 from Microsoft Update Catalog
Download KB4013418 from Microsoft Update Catalog
Direct download
This update includes quality improvements. No new operating system features are being introduced in this update. Key changes include:
- Addressed known issue called out in KB3213986. Users may experience delays while running 3D rendering apps with multiple monitors.
- Addressed issue in KB3213986 where the Cluster Service may not start automatically on the first reboot after applying the update.
- Addressed issue where the Active Directory Administrative Center (ADAC) crashes when attempting to modify any attribute of any user account in Active Directory.
- Addressed issue where the Japanese Input Method Editor is leaking graphics device interface resources, which causes windows to disappear or only partially render after typing approximately 100 sentences.
- Addressed an issue which improves the reliability of Enable-ClusterS2D PowerShell cmdlet.
- Addressed an issue where the Virtual Machine Management Service (Vmms.exe) may crash during a live migration of virtual machines.
- Improved the bandwidth of SSD/NVMe drives available to application workloads during S2D rebuild operations.
- Addressed issue where Work Folders clients get duplicate files (sync conflict files) when Work Folders is configured using Group Policy.
- Addressed an issue where Remote Desktop Servers crash with a Stop 0x27 in RxSelectAndSwitchPagingFileObject when RDP clients connect and utilize redirected drives, printers, or removable USB drives.
- Addressed issue where adjusting the Windows Server Update Services settings using the Group Policy feature causes downloads to fail.
- Addressed issue to hard code Microsoft's first-party provider registry key values.
- Addressed issue that causes the System Preparation (Sysprep) tool to fail.
- Addressed issue that causes Office 2016 profile corruption when used with User Experience Virtualization (UE-V) roaming.
- Addressed issue that causes the Local Security Authority Subsystem Service to become unresponsive after upgrading the OS.
- Addressed issue that causes the Local Security Authority Subsystem Service to fail when a SAP® application uses Transport Layer Security authentication.
- Addressed issue where sequencing large registries using the Application Virtualization 5.1 Sequencer results in missing registry keys in the final package.
- Addressed issue that fails to retain the sort order of names in a contact list after a device restarts when using the Japanese language.
- Addressed issue that causes transactions to fail because of a memory shortage.
- Addressed issue that allows files that are forbidden by the security zone setting to be opened in Internet Explorer.
- Addressed issue that causes Internet Explorer 11 to fail after installing KB3175443.
- Addressed issue that causes applications that use the VBScript engine to fail after applying KB3185319.
- Addressed issue that occurs in Internet Explorer when the CSS float style is set to "center" in a webpage.
- Addressed issue that occurs whenever the multipath IO attempts to log I/O statistics with no paths present.
- Addressed issue that causes a 32-bit static route added by a VPN solution to fail, which prevents users from establishing a connection through the VPN.
- Addressed issue that may decrease performance by up to 50% when Ethernet adapters that support receive side scaling (RSS) fail to re-enable RSS after a fault or system upgrade.
- Addressed issue to allow wildcards in the Allowed list field for the Point and Print Restrictions Group Policy.
- Addressed issue with multipath I/O failure that can lead to data corruption or application failures.
- Addressed issue that can lead to system failure when removing a multipath IO ID_ENTRY.
- Addressed issue that occurs when a Network Driver Interface Specification function NdisMFreeSharedMemory() is not called at the correct Interrupt Request Level.
- Addressed issue to utilize the proper service vault for Azure Backup integration.
- Addressed issue where SQL server takes 30 minutes to shut down on machines with a lot of RAM (>2TB).
- Addressed additional issues with updated time zone information, Internet Explorer, file server and clustering, wireless networking, Map apps, mobile upgrades for IoT, display rendering, USB 2.0 safe removal, multimedia, Direct3D, Microsoft Edge, enterprise security, Windows Server Update Services, storage networking, Remote Desktop, clustering, Windows Hyper-V, and Credential Guard.
- Security updates to Microsoft Edge, Internet Explorer, Microsoft Graphics Component, Internet Information Services, Windows SMB Server, Microsoft Windows PDF Library, Windows kernel-mode drivers, Microsoft Uniscribe, the Windows kernel, DirectShow, the Windows OS, and Windows Hyper-V.
If you installed earlier updates, only the new fixes contained in this package will be downloaded and installed on your device.
Known issues in this update
Microsoft is not currently aware of any issues with this update.
How to get this update
This update will be downloaded and installed automatically from Windows Update. To get the stand-alone package for this update, go to the Microsoft Update Catalog website.
- Update replacement information This update replaces the previously released update KB4010672.
- File information For a list of the files that are provided in this update, download the file information for cumulative update KB4013429. If you're installing a Windows 10 update for the first time, the package size for the X86 version is 579 MB and the package size for the x64 version is 1,105 MB.
Download KB4013429 from Microsoft Update Catalog
Download KB4013418 from Microsoft Update Catalog
Direct download
- windows10.0-kb4013429-x64.msu
- windows10.0-kb4013429-x86.msu
- windows10.0-kb4013429-x64.cab
- windows10.0-kb4013429-x86.cab
- windows10.0-kb4013418-x64.msu
- windows10.0-kb4013418-x86.msu
- windows10.0-kb4013419-x64.cab
- windows10.0-kb4013419-x86.cab
- windows10.0-kb4013429-x64_delta.msu 699,8 MB
- windows10.0-kb4013429-x86_delta.msu 357,0 MB
thanks for your extensive insides and information! I have a problem installing these , am trying for three straight days now , but I keep getting an error , not on the downloading part , but on the install end....and yes I have tried the windows update repair tool to try and fix the problems ( tool told me that several errors where resolved , but no prevail! )
Hi daniel! I did as you suggested before , but it still keeps giving me the same error code (0x800705b4) as before and cannot install the updates 😞
@Starrchild1976 wrote:Try this tool from Microsoft: https://support.microsoft.com/en-ca/instantanswers/512a5183-ffab-40c5-8a68-021e32467565/windows-update-troubleshooter
Hi daniel! I did as you suggested before , but it still keeps giving me the same error code (0x800705b4) as before and cannot install the updates :(
If that doesn't work you may need to visit the Microsoft Community and the Windows Experts will help you: https://answers.microsoft.com/en-us/windows/forum/windows_10
https://www.thegeneralistit.com/blog/2015/10/02/fixing-windows-10-update-error-0x800705b4/
thank you for being so patient with me : I will try the steps ( links ) you have provided me with , so fingers crossed the update will eventually run after this. if not I will revert back to the baseline snapshot with rollback rx. or use the media creation tool. the funny thing is when I search the microsoft community for the error code the answer lies within windows defender update ( I have defender disabled via group policies , so I am a bit confused here ) o yes also trying the sfc/scannow command prommt to see if this brings any salvage 🙂
None of the solutions did work , sfc scannow did not find any problems....so I am going to download the latest media creation tool to solve this mess! Thanks Daniël for all your tips it is very , very much apreciated mate!!!!!!
SOLUTION FOUND to cumulative update KB4013429. Tried everything many times over three days: repairing system files, refreshing components from ISO, stand-alone update, etc. etc. and still the message: "failed to update..undoing changes...".
Problem solved by downloading script to reset Windows Update: "resetWUeng.cmd" from this link: https://gallery.technet.microsoft.com/scriptcenter/Reset-Windows-Update-Agent-d824badc
System successfully upgraded from 10.14393.693 to 10.14393.953 - The only thing that worked for me !!!
Problem solved by downloading script to reset Windows Update: "resetWUeng.cmd" from this link: https://gallery.technet.microsoft.com/scriptcenter/Reset-Windows-Update-Agent-d824badc
System successfully upgraded from 10.14393.693 to 10.14393.953 - The only thing that worked for me !!!
Reply
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.