Vulnerability in Internet Explorer Could Allow Remote Code Execution
Yesterday, Microsoft announced a remote code execution vulnerability in Internet Explorer which utilizes memory in a way that allows the execution of malicious code and installs the Poison Ivy backdoor trojan. It exploits a use-after-free vulnerability in IE which allows the "badguys" to create an image URL that accesses the uninitialized memory. As of now the attacks are targeting Windows XP systems but with the use of Metasploit code, it would not be suprising to see the attacks on other platforms as well.
Microsoft is encouraging that all users enable a firewall, apply ALL software updates, and to install an anti-virus and anti-spy-ware program. These types of vulnerabilities are common with MS products and are seen all the time. If you keep Java and Microsoft up-to-date, and you have Webroot SecureAnywhere, you will still be protected from malware that may slip through these holes. :D
Anti-virus is essential, although using a different browser until a security update is released can help, you are still vulnerable, this attack exploits IE code, which is used by multiple utilities and third-party applications you use every day.
Yunsun Wee, director, Microsoft Trustworthy Computing recommends that you keep Java up-to-date or that you uninstall it altogether and that using EMET 3.0 can help protect Windows systems and older operating systems such as XP in particular. You can always run EMET alongside Webroot for an added layer of protection although it is not necessary.
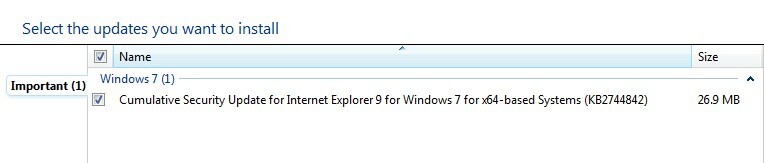
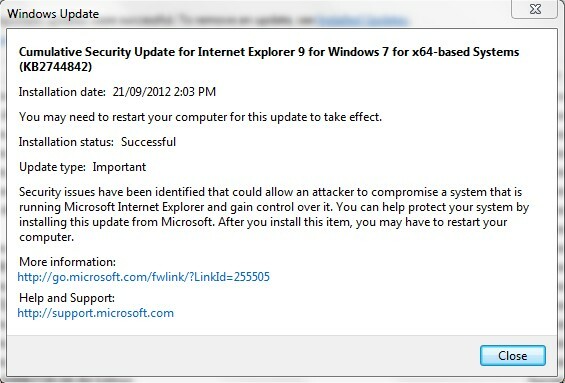
Here is the full security advisory from Microsoft.
Vulnerability in Internet Explorer Could Allow Remote Code Execution
Published: Monday, September 17, 2012