An attacker going by the name of Harak1r1 is hijacking unprotected MongoDB databases, stealing their content, and asking for a Bitcoin ransom to return the data.
These attacks have been happening for more than a week and have hit servers all over the world. The first one to notice the attacks was security researcher Victor Gevers, who, as part of Project 366 with the GDI Foundation, has been busy searching for unprotected MongoDB servers and alerting companies about their status.
Full Article
More information here:
Emory Healthcare patient data hijacked and held for ransom?
By Dissent, 4th January 2017
Gevers originally indicated that there were a few hundred affected databases, but by yesterday afternoon, John Matherly, the founder of Shodan.io, tweeted that there were now nearly 2,000 such instances of Harak1r1 hijacking databases for ransom.
By early this afternoon, that number had reportedly risen to 3,500, and there appeared to be 17 payment transactions to the specified Bitcoin wallet, suggesting that at least some of the victims are choosing to pay the ransom. The first payment to the BTC wallet was made on December 21.
On December 30, MacKeeper Security Research Center discovered yet another misconfigured MongoDB installation that contained what appeared to be hundreds of thousands of patient records and other sensitive information of Emory Healthcare patients. The IP address of the misconfigured database reversed to clinicworkflow.org, a domain that was first registered on November 13, 2016 and that is linked to Emory Brain Health Center.
Full Article
Emory Healthcare patient data hijacked and held for ransom?
By Dissent, 4th January 2017
Gevers originally indicated that there were a few hundred affected databases, but by yesterday afternoon, John Matherly, the founder of Shodan.io, tweeted that there were now nearly 2,000 such instances of Harak1r1 hijacking databases for ransom.
By early this afternoon, that number had reportedly risen to 3,500, and there appeared to be 17 payment transactions to the specified Bitcoin wallet, suggesting that at least some of the victims are choosing to pay the ransom. The first payment to the BTC wallet was made on December 21.
On December 30, MacKeeper Security Research Center discovered yet another misconfigured MongoDB installation that contained what appeared to be hundreds of thousands of patient records and other sensitive information of Emory Healthcare patients. The IP address of the misconfigured database reversed to clinicworkflow.org, a domain that was first registered on November 13, 2016 and that is linked to Emory Brain Health Center.
Full Article
January 5, 2017 By Catalin Cimpanu
According to the MacKeeper Security Research Team, Harak1r1 had ransacked and blocked Emory's access to more than 200,000 medical records.
Attacks from harak1r1 went on for two more days, but as worldwide infosec media started covering the topic, two copycats appeared and started doing the same.
The second group goes by the name of 0wn3d, and they work by replacing the hijacked database tables with a table named WARNING_ALERT.
A day later, the same Gevers came across a third actor, using the name 0704341626asdf, which appears to have hit over 220 MongoDB servers.
Full Article
Victor Gevers@0xDUDEPlease STOP paying the ransom. There is no evidence that they actual copied your database. Get a local expert to have your log files checked https://twitter.com/WeAreLighten/status/816944495669420032 …10:18 AM - 5 Jan 2017
According to the MacKeeper Security Research Team, Harak1r1 had ransacked and blocked Emory's access to more than 200,000 medical records.
Second group joins the scene
Attacks from harak1r1 went on for two more days, but as worldwide infosec media started covering the topic, two copycats appeared and started doing the same.
The second group goes by the name of 0wn3d, and they work by replacing the hijacked database tables with a table named WARNING_ALERT.
Third group discovered
A day later, the same Gevers came across a third actor, using the name 0704341626asdf, which appears to have hit over 220 MongoDB servers.
Full Article
Posted by Dissent, 7th January 2017
Gevers and Niall Merrigan are finding evidence that although the hackers claim they have saved your data and will return it, for the most part, that is not what is happening. What is happening, the researchers claim, is that the data are just being wiped. There appears to be one attacker who may be saving some of the data, but overall, this now appears to be a tremendous scam where attackers claim to have stolen your data, and if you’ll just pay them, you’ll get it back, when in reality, they’ve just deleted your data. Why should they pay for all that storage space, right, if they can get you to send them about $200 in a panic?
As of the time of this posting, there have been about 12 accounts/attackers, each with its own email address and bitcoin wallet(s), and there have been more than 11,253 MongoDB installations that have been wiped in the past few weeks.
Full Article
Gevers and Niall Merrigan are finding evidence that although the hackers claim they have saved your data and will return it, for the most part, that is not what is happening. What is happening, the researchers claim, is that the data are just being wiped. There appears to be one attacker who may be saving some of the data, but overall, this now appears to be a tremendous scam where attackers claim to have stolen your data, and if you’ll just pay them, you’ll get it back, when in reality, they’ve just deleted your data. Why should they pay for all that storage space, right, if they can get you to send them about $200 in a panic?
As of the time of this posting, there have been about 12 accounts/attackers, each with its own email address and bitcoin wallet(s), and there have been more than 11,253 MongoDB installations that have been wiped in the past few weeks.
Full Article
Thanks for posting the warning about this one...as it easy to see how panicking users could be easily duped by this bit of 'psychological' twist to what would already be a very stressful situation to be in. It appears that these miscreants have no morals of any kind and are also **bleep** lazy to boot. :@
This is getting ridiculous with MongoDB, at present things appear to be going a loittle bit out of control with the increasing amount of attacks.
Over a quarter of MongoDB databases left open to the internet have been ransacked by online extortionists.
By Liam Tung | January 9, 2017
According to Merrigan, some 27,000 MongoDB servers have been compromised in the past day, up from an estimated 2,000 on January 3 and 8,542 on January 5.
MongoDB is a popular open-source NoSQL database, widely used for big data and analytics. On the DB-Engines Ranking of database popularity it stands in fourth spot out of 315 systems, behind only Oracle, MySQL, and Microsoft SQL Server.
Full Article
Over a quarter of MongoDB databases left open to the internet have been ransacked by online extortionists.
By Liam Tung | January 9, 2017
According to Merrigan, some 27,000 MongoDB servers have been compromised in the past day, up from an estimated 2,000 on January 3 and 8,542 on January 5.
MongoDB is a popular open-source NoSQL database, widely used for big data and analytics. On the DB-Engines Ranking of database popularity it stands in fourth spot out of 315 systems, behind only Oracle, MySQL, and Microsoft SQL Server.
Full Article
A good article from Brian Krebs on the subject.
10th January 2017
This blog has featured several stories over the years about companies accidentally publishing user data via incorrectly configured MongoDB databases. In March 2016, for example, KrebsOnSecurity broke the news that Verizon Enterprise Solutions managed to leak the contact information on some 1.5 million customers because of a publicly accessible MongoDB installation.
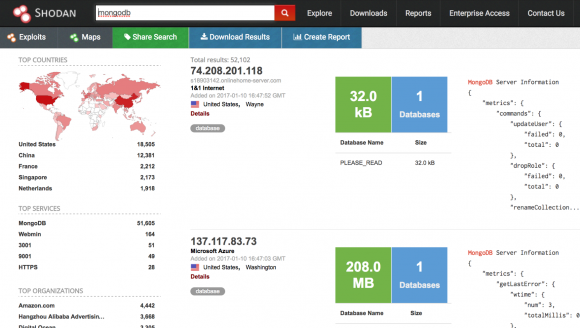
Shodan, a specialized search engine designed to find things that probably won’t be picked up by Google, lists the number of open, remotely accessible MongDB databases available as of Jan. 10, 2017.
Point is, this is a known problem, and almost once a week some security researcher is Tweeting that he’s discovered another huge open MongoDB database. There are simple queries that anyone can run via search engines like Shodan that will point to all of the open MongoDB databases out there at any given time. For example, the latest query via Shodan (see image above) shows that there are more than 52,000 publicly accessible MongoDB databases on the Internet right now. The largest share of open MongoDB databases are here in the United States.
Full Article
10th January 2017
This blog has featured several stories over the years about companies accidentally publishing user data via incorrectly configured MongoDB databases. In March 2016, for example, KrebsOnSecurity broke the news that Verizon Enterprise Solutions managed to leak the contact information on some 1.5 million customers because of a publicly accessible MongoDB installation.
Shodan, a specialized search engine designed to find things that probably won’t be picked up by Google, lists the number of open, remotely accessible MongDB databases available as of Jan. 10, 2017.
Point is, this is a known problem, and almost once a week some security researcher is Tweeting that he’s discovered another huge open MongoDB database. There are simple queries that anyone can run via search engines like Shodan that will point to all of the open MongoDB databases out there at any given time. For example, the latest query via Shodan (see image above) shows that there are more than 52,000 publicly accessible MongoDB databases on the Internet right now. The largest share of open MongoDB databases are here in the United States.
Full Article
Stop right now and make sure you've configured it correctly
11 Jan 2017 By Thomas Claburn
MongoDB, like other NoSQL databases, has suffered from security shortcomings for years. Trustwave called out MongoDB in 2013. Security researcher John Matherly did so again in 2015.
Where MySQL, PostgreSQL, and other relational databases tend to default to local installation and some form of authorization, MongoDB databases are exposed to the internet by default, and don't require credentials immediately by default.
MongoDB's post explains "how to avoid a malicious attack that ransoms your data," but it does so by directing database users to take responsibility for configuring the software securely.
Full Article
Reply
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.