Serious security hole in Gmail password reset system found by security researcher
A security researcher has uncovered what Google has described as a “high impact” bug in its account recovery process, which could have potentially allowed hackers to trick users into handing over their passwords.
White-hat hacker Oren Hafif found the security hole, which has now been fixed by Google.
On his blog, Hafif describes how the security hole could be exploited, and made a video (blessed with a suitably funky beat) demonstrating how it could work.
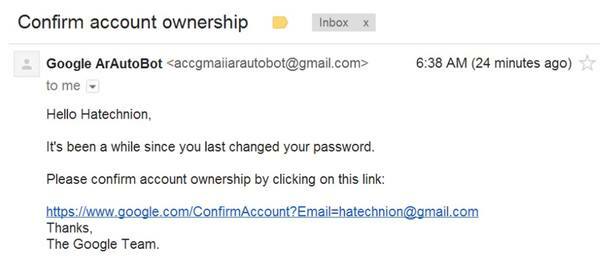
Hafif’s demonstration of how to steal a Google password starts simply enough – with a fairly normal looking phishing email, claiming to come from Google.
Full Topic
Google engineers have squashed several high-impact security vulnerabilities in the company's account recovery system that enabled attackers to hijack user accounts.
A proof-of-concept attack that exploited the bugs required a victim to click a booby-trapped link leading to Google.com contained in a spear phishing e-mail. Behind the scenes, the link briefly redirected to an attacker's website even as it opened a legitimate password-reset page on Google. When a victim clicked on the link while logged in to the targeted Gmail account, the attacker site also performed a cross-site scripting attack. The Web application equivalent of a Jedi mind trick, the two exploits sent both the password entered by the victim and the authentication cookie used to access the account to the attacker's website.
"It's a clever attack," Jeremiah Grossman, CTO of Web-application security firm WhiteHat Security, told Ars. "There's elegance and simplicity." The exploit developer "did a lot of work behind the scenes to make the attack simple. This is what we're meant to do in a browser on Gmail. When we see links, we're meant to click on them."
Full Topic
A proof-of-concept attack that exploited the bugs required a victim to click a booby-trapped link leading to Google.com contained in a spear phishing e-mail. Behind the scenes, the link briefly redirected to an attacker's website even as it opened a legitimate password-reset page on Google. When a victim clicked on the link while logged in to the targeted Gmail account, the attacker site also performed a cross-site scripting attack. The Web application equivalent of a Jedi mind trick, the two exploits sent both the password entered by the victim and the authentication cookie used to access the account to the attacker's website.
"It's a clever attack," Jeremiah Grossman, CTO of Web-application security firm WhiteHat Security, told Ars. "There's elegance and simplicity." The exploit developer "did a lot of work behind the scenes to make the attack simple. This is what we're meant to do in a browser on Gmail. When we see links, we're meant to click on them."
Full Topic
Reply
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.