By: HNS Staff/ Posted on 07.08.2014
Turla, also known as Snake or Uroburos is one of the most sophisticated ongoing cyber-espionage campaigns. When the first research on Turla/Snake/Uroburos was published, it didn’t answer one major question: how do victims get infected?
The latest Kaspersky Lab research on this operation reveals that Epic is the initial stage of the Turla victim infection mechanism.
http://www.net-security.org/images/articles/turla-07042014.jpg
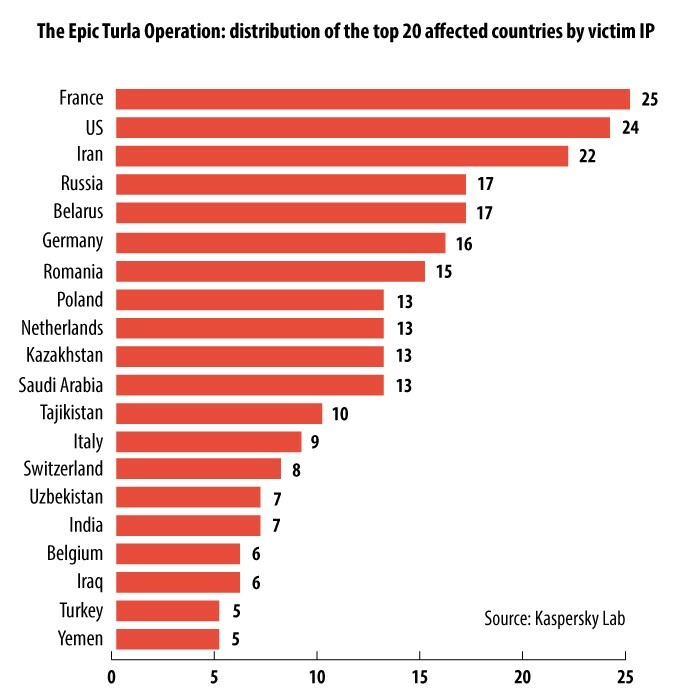
The “Epic” project has been used since at least 2012, with the highest volume of activity observed in January-February 2014. Most recently, Kaspersky Lab detected this attack against one of its users on August 5, 2014. The attacks are still ongoing, actively targeting users in Europe and the Middle East.
Help Net Security/ Full Article Here/ http://www.net-security.org/malware_news.php?id=2832
August 8th, 2014, 18:30 GMT · By Ionut Ilascu
Security experts analyzing a cyber-espionage campaign found that the largest number of websites infected with malware that leads to distributing the Turla Trojan were administrated by the Romanian Government.
Named by Kaspersky researchers “Epic Turla,” the espionage campaign that relies on the Turla toolkit (also known as Snake or Uroburos) distributes the spying component through spear-phishing and watering hole attacks.
It seems that in the case of the latter, in a classification per country, Romania is at the top of the list with 17 websites injected with the malware-serving code. This by far is the largest number of infections, since the next most affected country, Switzerland, recorded almost half the amount, nine.
Full Article
Security experts analyzing a cyber-espionage campaign found that the largest number of websites infected with malware that leads to distributing the Turla Trojan were administrated by the Romanian Government.
Named by Kaspersky researchers “Epic Turla,” the espionage campaign that relies on the Turla toolkit (also known as Snake or Uroburos) distributes the spying component through spear-phishing and watering hole attacks.
It seems that in the case of the latter, in a classification per country, Romania is at the top of the list with 17 websites injected with the malware-serving code. This by far is the largest number of infections, since the next most affected country, Switzerland, recorded almost half the amount, nine.
Full Article
Reply
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.