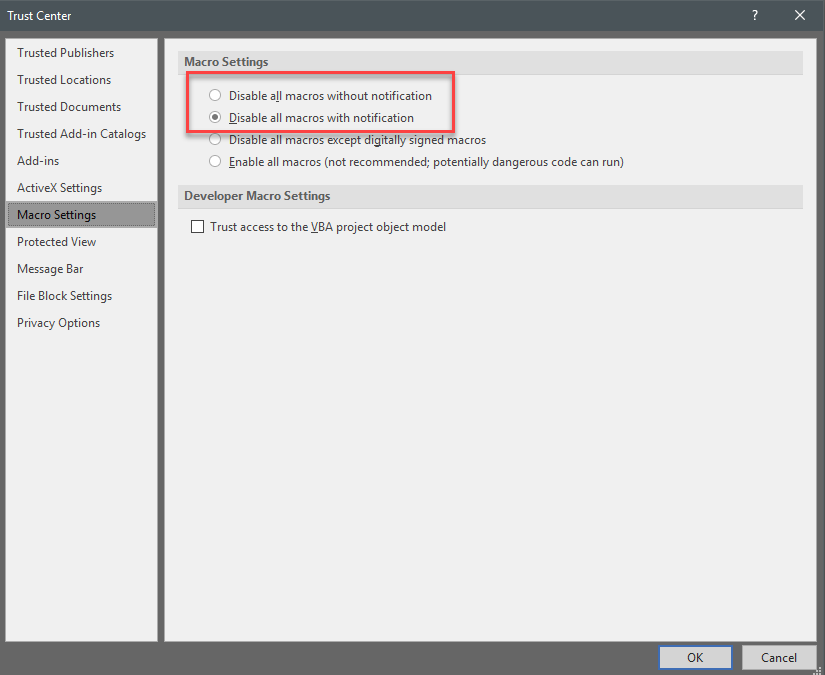
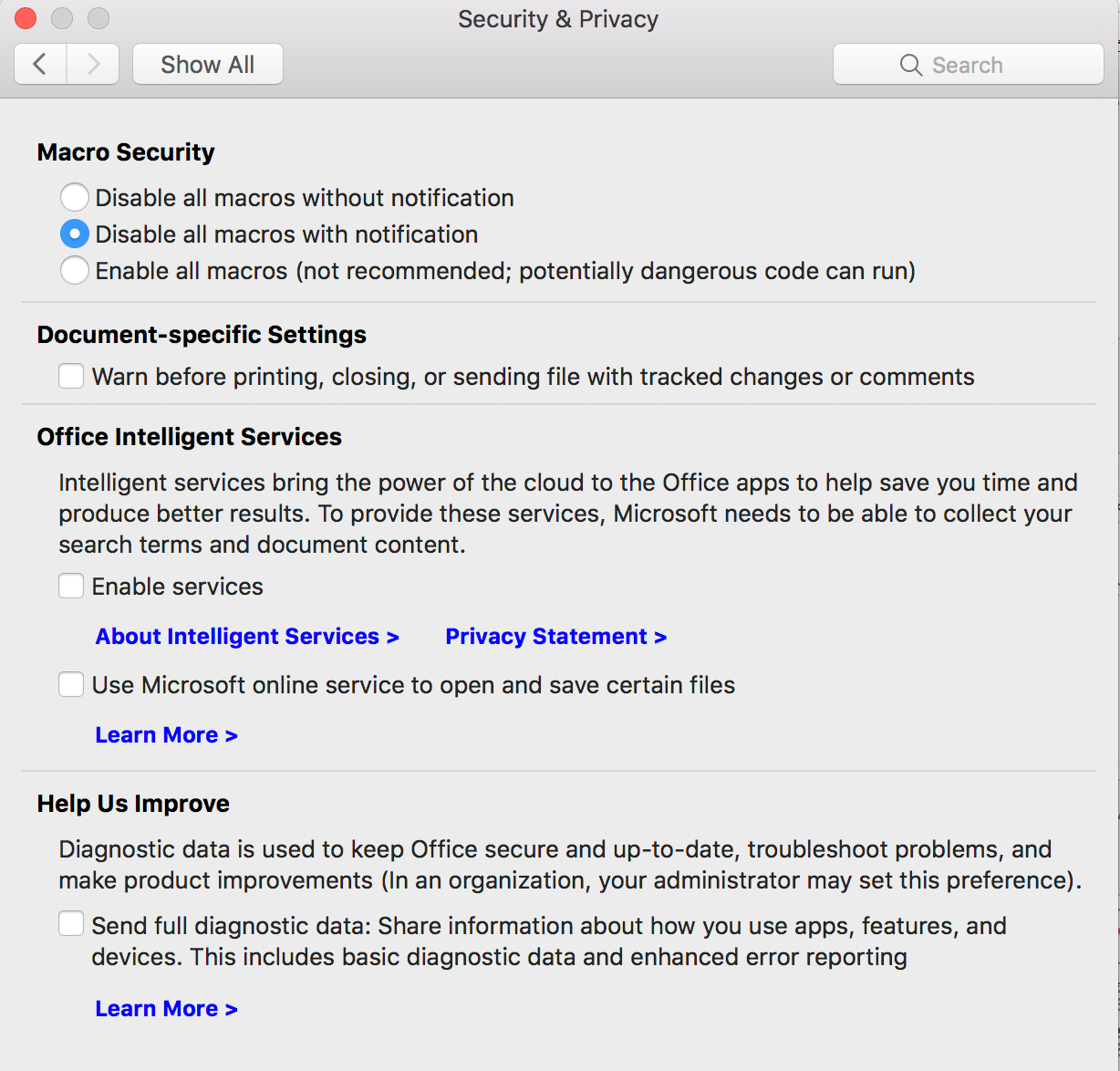
Using Microsoft Powerpoint as Malware Dropper
This is one of the many reasons I'm transferring all my Microsoft Office documents to iWork documents on the Mac. ;)
All you have to do is make sure Macros are disabled within Office!@ wrote:
This is one of the many reasons I'm transferring all my Microsoft Office documents to iWork documents on the Mac. ;)
Reply
Login to the community
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.