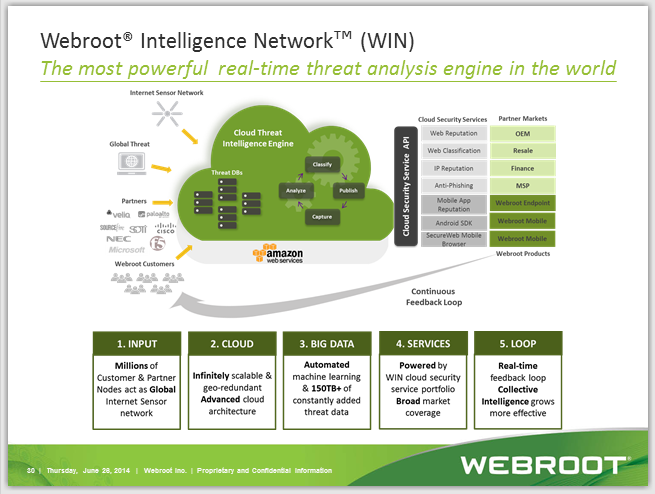
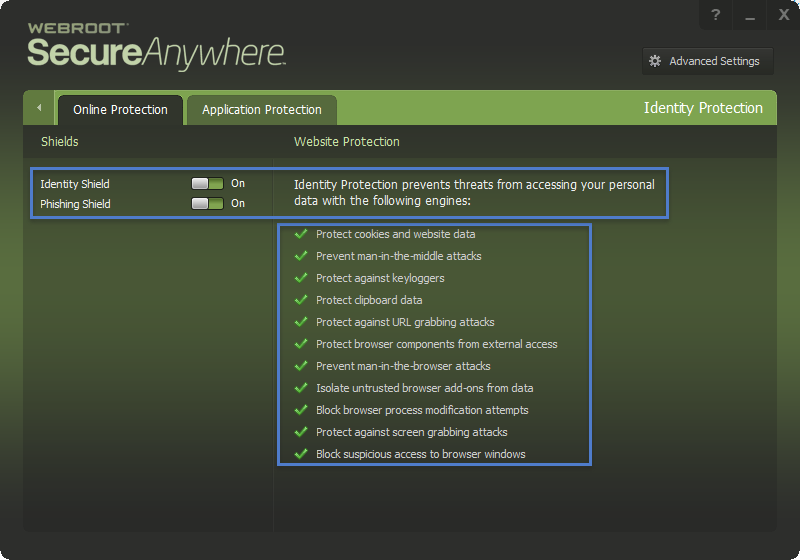
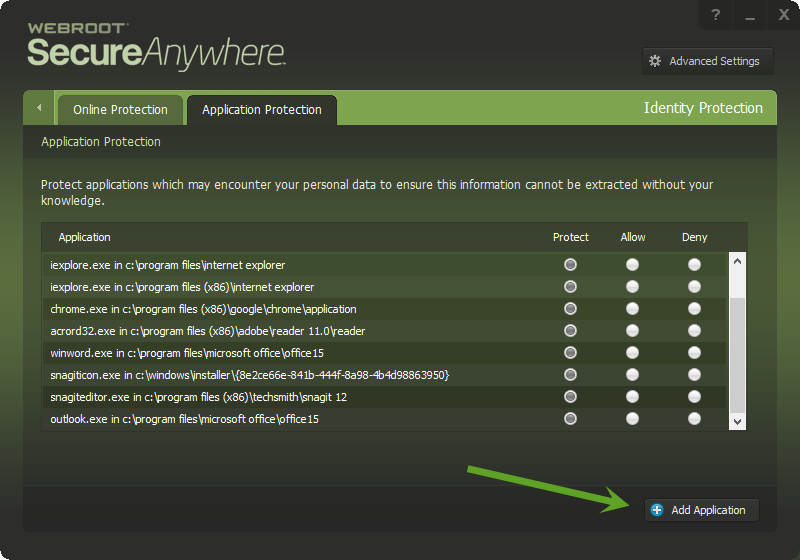
Can you please confirm that this (unknown and undetected) keylogger would be automatically blocked from sending the captured keystrokes to a remote server? i.e. would the Webroot firewall component prompt me before allowing an unknown (as yet unverified) application from connecting outbound?
Thanks
PJ
Best answer by DanP
View original