The next attack in our series on the diverse methods hackers use to phish their targets has earned the ire of the FBI. It’s the source of over a billion dollars of lost revenue for businesses and, not surprisingly, a method favored by cybercriminals for its low-effort, high-return paybacks.
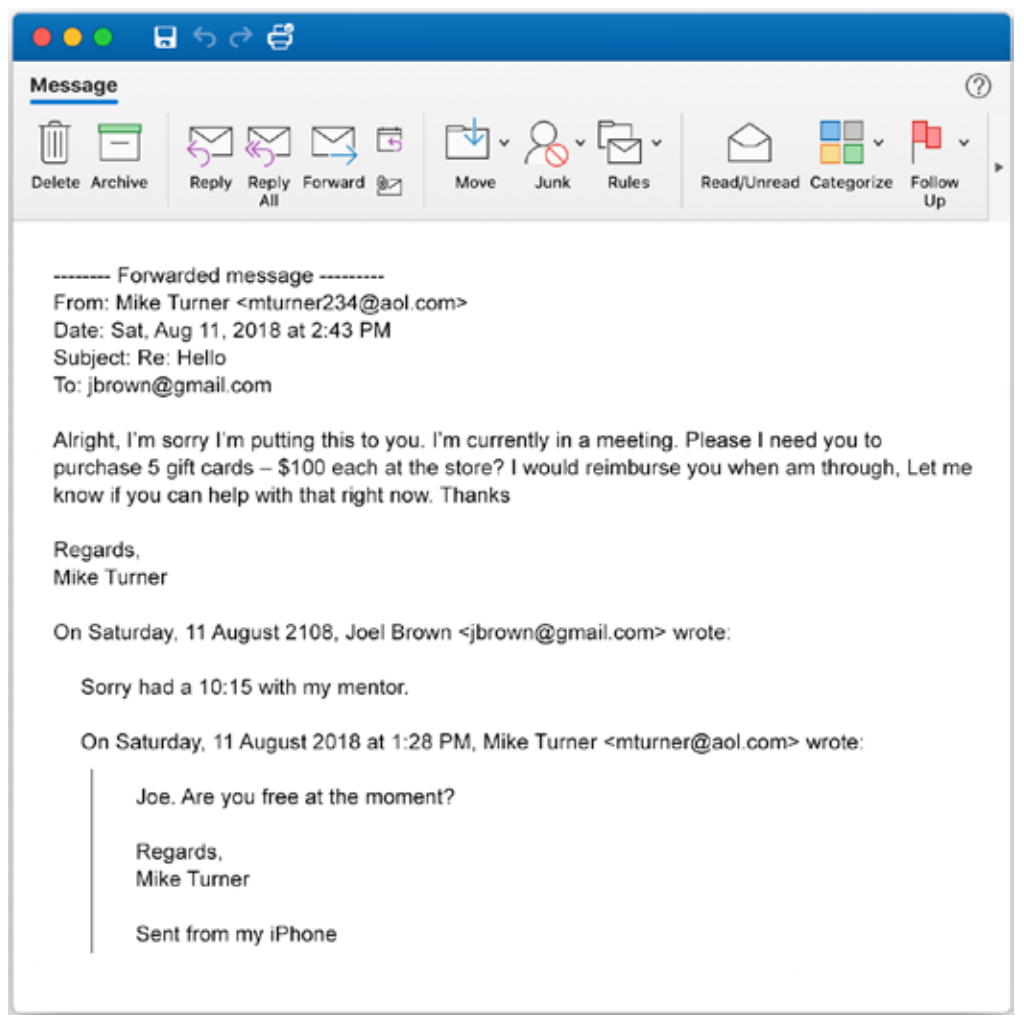
One of the most expensive threats facing businesses today, business email compromise involves a phony email, usually claiming to be someone from within or associated with a target's company, requesting a payment or purchase be made (often of gift cards). A "confidence game" according to the FBI, BEC attempts are often accompanied by a sense of high urgency to discourage critical thinking.
FYI: Of the $3.5 billion the FBI estimates businesses lost to cybercrime in 2019, nearly half ($1.7 billion) was blamed on business email compromise.
The Classic BEC Scheme
One of the most famous templates for achieving business email compromise is a frantic request by a supposed superior for gift cards. Often supported by publicly available information like a recently closed business deal, these common attacks ask for a rush delivery of gift cards from a large retailer be delivered to an address controlled by the malicious actor.
Look familiar? “As a thank you to X client, I need you to mail $3 thousand in Target gift cards to their head of procurement ASAP!"



