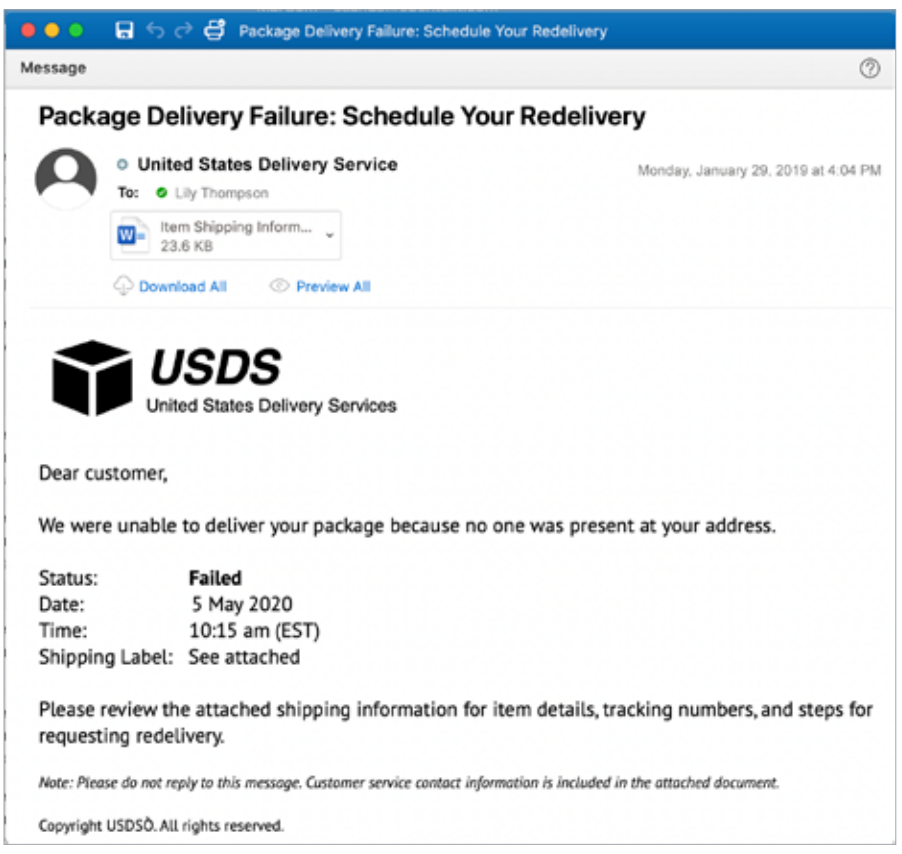
Next up in our series on the diverse types of phishing now used by cybercriminals, we come to malware phishing. Using the same techniques, this type of phishing introduces nasty bugs by convincing a user to click a link or download an attachment so malware can be installed on a machine. It is currently the most widely used form of phishing attacks.
SIM swapping is a type of spear phishing where attackers phish a target’s phone carrier, pretending to be the target to replace the SIM card with one of their own. One such case resulted in $24 million of lost cryptocurrency.
Tip: Received an unsolicited email from an unknown sender? Beware of downloading anything sent along with it. Many are malicious attachments known as ‘macros.’
How to Spot Malware Phishing
One hallmark of malware phishing is the attachment of a blank document requiring you to enable macros to view its contents. This is a major red flag.