The education sector has unique cybersecurity challenges compared to sectors like healthcare or finance. While malicious activity is usually directed at schools and third level education, online education and various other bodies can find themselves in the crosshairs of malware attacks. As expected, this sector has also become a target for cybercriminals looking to cash in on limited IT resources and a broad attack surface.
State of the Sector
From a cybersecurity point of view, education performs poorly. According to Microsoft Security Intelligence, 61% of malware encounters have hit the education sector. (Source)
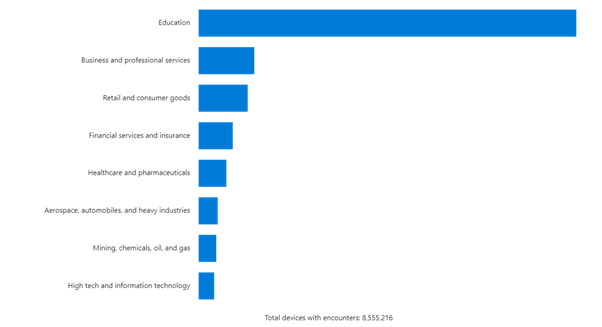
Microsoft Security Intelligence found that 61 percent of nearly 7.7 million enterprise malware encounters reported in the past month came from those in the education sector, making it the most affected industry
America’s K-12 system (“public kindergarten to 12th grade” roughly comparable to 5 – 18 years of age within the UK education system) releases a security report each year through the K-12 Cybersecurity Resource Center. They have reported a consistent and steep increase of cyber-related incidents year-over-year beginning from 2016 to the present. (Source)
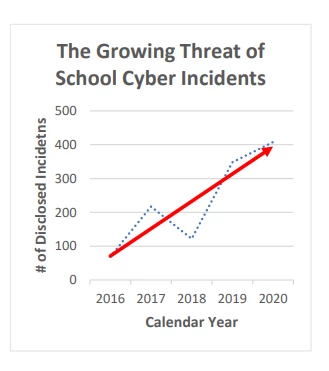
The State Of K-12 Cybersecurity: 2020 Year in Review
In the UK, the National Cyber Security Centre (NCSC) constantly issues alerts. The centre is particularly worried about a recent surge in ransomware attacks, as UK schools remain a prime target of malicious actors.
Notable Types of Attacks
BEC Scams
Business email compromise (BEC) attacks involve scamming unsuspecting users for money. BEC attacks occur when a malicious actor sends fraudulent emails. It is one of the largest types of cybercrime in the world. (Source)
Many cybercriminals exclusively target educational institutions. For example, in the United States, threat actors went after the University of California, San Diego, and the University of Pennsylvania. Threat actors in Kenya managed to scam hundreds of thousands of dollars from these institutions. (Sour ce) In Ireland, Trinity College and the Louth and Meath Education and Training Board were both hit by similar attacks. (Source)
Ransomware
Ransomware, along with BEC attacks, consistently remain top cybercrime attacks.vivii Schools are particularly vulnerable to ransomware due to security weaknesses. Schools also remain vulnerable because ransomware attacks can be timed during examinations or registration periods.viii NCSC and other security groups have issued alerts about the recent surge of ransomware.
The cost of ransom is steep. The average ransom demanded is over £120,000 pounds ($170,000 USD). According to research from Carbonite + Webroot, OpenText companies, the true cost of ransomware is far greater. This figure doesn’t include damages to operations, reputation, insurance or the cost of defensive measures. (Source)
Data Theft
Data loss from theft is a frequent occurrence for schools. Personal data is readily traded and visible on the marketplace within the dark web. (Source)
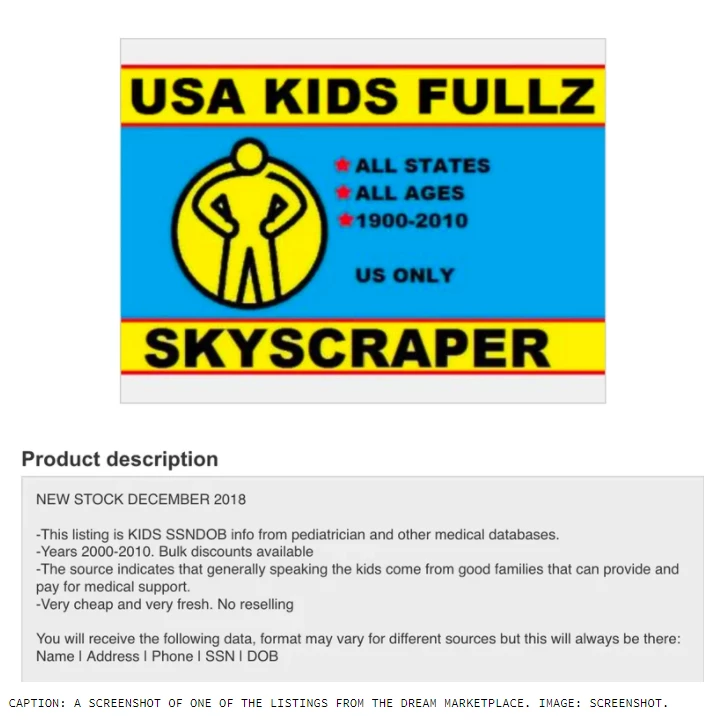
Ransomware attackers today are also likely to steal data for financial gain or to extort their victims. (Source) According to research from Carbonite + Webroot, the cost of 100 stolen records is between $18K – $35K USD. (Source)
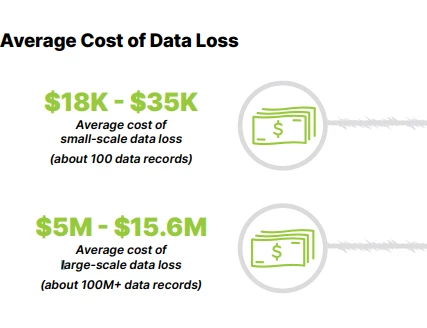
The Hidden Costs of Ransomware. Carbonite + Webroot, OpenText companies, 2021
Stolen data in these cases often include valuable research or intellectual property targeted by nation-state hackers.(Source) For example, medical research data can take years to develop but can be stolen in a matter of minutes. The motivation behind stealing medical research may vary, but one of the major underlying reasons is financial gain. Some attacks could be state-sponsored initiatives to outpace other nations in the pharmaceutical sector.(Source)
Challenges to Protecting Education
Lack of Security Awareness and Training
A survey published by the National School Boards Association in the United States found that school officials are less prepared for cyberattacks than their peers within the private sector.(Source) The move to remote work has caught many teachers off guard.
Shadow IT
It is not uncommon for school administrators or teachers to make technology purchases without the consent or even knowledge of the system’s technology department. In these cases, equipment and software are purchased with little to no consideration of the potential cybersecurity risks.
Sprawling, Disjointed Networks
A single college or school campus might contain many different sub-organisations, such as offices or departments.
Disparate Devices
The global standardization of devices in remote teaching is almost non-existent. Even in countries like Ireland, where most schools are run by the same state department. Insecure teaching and IoT equipment can provide an easy way for a malicious actor to gain a foothold onto a network.
COVID-19/Remote Work
The current COVID-19 pandemic has resulted in significant changes to the workforce and the way individuals conduct their lives in general. The rise in work from home (WFH) has led to many challenges for security administrators. Many schools and colleges have been thrown into remote working and teaching without the proper security protocols in place to protect the learning environment.
Remote Learning Tools
The growth in remote learning has increased a school’s vulnerability to cyberattacks. In cases where all learning takes place online, serious attacks can halt the learning process for students. In March 2021, numerous schools within the Nottinghamshire district had to shut down their information technology infrastructures because of a sophisticated cyberattack.(Source)
Remote learning has also led to increased risk. For instance, when a school suddenly decides to move its learning online, users without the proper training or knowledge may attempt to come up with their own solutions, which can pose security risks.
Some of these risky practices include:
-
Using a private messenger service
-
Sending files to each other through personal email addresses
-
Setting up video conferencing using free software or applications
It is the responsibility of IT administrators to provide proper procedures that service the new environments adequately and securely by providing proper training, monitoring, and compliance.(Source)
Remote Administrators
Attackers frequently target an organisation’s networks through remote access systems, such as remote desktop protocol (RDP) and virtual private networks (VPN).
Malicious actors regularly exploit:
-
Weak passwords
-
Lack of multi-factor authentication (MFA)
-
Unpatched vulnerabilities
The use of unsecured RDP has grown exponentially as more administrators work from remote locations. Between January and March 2020, approximately three to four and half million ports were exposed.(Source)
Mitigation and NCSC Advice
-
Layer cybersecurity defences. AV, firewalls, email-filtering, intrusion detection or DNS protection. All offer immense protection when stacked or layered.
-
Mandating two-factor authentication (2FA) wherever possible. While 2FA isn’t the end of security issues, it makes things more difficult for cybercriminals at every turn.
-
Audit and control software and devices. This might sound tough in a chaotic environment like a school where there is a lot of BYOD, but the first step should be monitoring and observing work practices before security guidelines are laid down. What video communication tool should be used for remote teaching? What file extensions should be allowed and will they just be sent by email (which probably has file scanning) or by a mobile chat app (which probably doesn’t)?
-
Talk to your IT and security vendors. You’re paying for security and IT so why not reach out to the experts and ask their opinion? If they are tough to get a hold of or don’t want to talk to you then consider getting a new vendor.
-
Secure RDP …and do it right away!
-
Train and test everybody. Training is an important part of the security puzzle as humans are most often the chink in any organisations armour. Train all staff and students and start from the top with school leaders and IT admins first. BEC scams often attack schools and colleges by breaching or impersonating senior staff. How can you tell training has been successful? Why not test users with simulated attacks?
-
Push patches and updates with urgency. Closing those gaps as soon as possible is an actionable step educational facilities can take to protect themselves and their users.
-
Back up everything. One of the most surefire ways of reducing the leverage an attacker has over you and your clients is keeping multiple backups of critical business data. Cybercriminals can’t be trusted to restore data even after a ransom is paid, so don’t be left relying on them.
-
Test your backup plan. The day disaster strikes is not the time to discover if your disaster recovery plan is well designed. Instead, simulate a worst-case scenario ahead of time and see if any gaps emerge.
https://www.ncsc.gov.uk/news/alert-targeted-ransomware-attacks-on-uk-education-sector



