More than half of British firms 'report cyber-attacks in 2019' – Hiscox
The insurer Hiscox has conducted research outlining a jump in reported attacks on UK businesses on last year. This 15% jump in incidents accompanies a 61% increase in average losses from breaches. This is something being reported across the board. As I mentioned recently a Coveware report has seen similarly huge rises in ransomware incidents. As well as putting out research on how companies are ill prepared, Hiscox have made the recent news for not paying out cyberinsurance claims. Specifically from the NetPetya attacks of 2016 that they argue were invalid due to the involvement of terrorism.
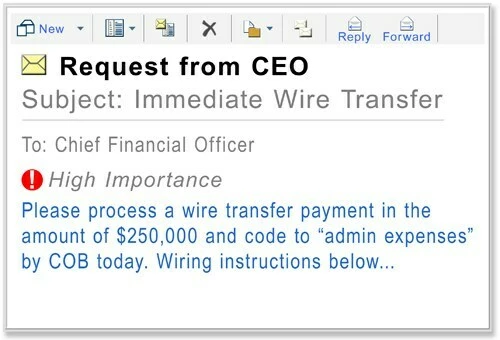
FBI: BEC Losses Surged to $1.3bn in 2018
BEC or Business Email Compromise scams aren’t among the most complicated cybercrime out there. In their very simplest form they involve fooling finance staff with spoofed emails. Despite this simplicity they accounted for over 20,000 of FBI reported cyber-attacks last year leading to losses of just under $1.3bn, the largest of any cybercrime type“. There are always tweaks to these cons to keep them dangerous. Last Christmas receptionists were targeted in huge campaigns asking them to pick up gift cards for “senior management” before it was realized the emails were faked. Google and Facebook were rinsed for €122 million by a Lithuanian BEC attacker who plead guilty to his crimes a month ago.
What can a company do to combat BEC?
User education is the main defense against these attacks. If your financial staff or CEOs are talking to an imposter who convinces them to wire cash then they really should have been more vigilant, no reasonable amount of email filtering is going to stop all fake emails getting through.
Emotet scales use of stolen email content for context-aware phishing
Emotet steals everything it can from a machine so it can spread and drop other nasty infections. Despite its effectiveness at stealing passwords and other data most were surprised to see it hoover up the actual contents of millions of emails late last year. Stealing the contents of emails can lead to valuable emails but it is a lot of data for crooks to sift through.
It turns out Emotet were using these stolen emails to increase the effectiveness and believability of their own phishing emails. The gang behind this malware and associated payloads are famous for being sophisticated and far-reaching so perhaps this technologically impressive move shouldn’t be too amazing. It is a step into the realm of what Webroot CTO Hal Lonas has warned about and that is the use of machine learning and AI by top cybercriminals.
Aebi Schmidt
As noted in this article this company joins Norsk Hydro as a recent large European victim of bad ransomware disruption. Similarly the recent targeting of the Luas (Dublin light rail) website shows that ransomware can be used to target specific business functions as well as the data shares it is usually associated with. The company has only made a Facebook message via a spokesperson because it’s email is down and there is no official message on the site yet.