Just updated to Mac Monterey 12.3 yesterday, and Webroot 9.5.0.139 detects Xprotect Remediator MRT v3 as Keylogger.Refog.1.r.
Can anyone verify this, please?
Thanks.
Best answer by ChadL
View originalJust updated to Mac Monterey 12.3 yesterday, and Webroot 9.5.0.139 detects Xprotect Remediator MRT v3 as Keylogger.Refog.1.r.
Can anyone verify this, please?
Thanks.
Best answer by ChadL
View originalInteresting enough when I received warning with different info:
Threat List:
.isn, PUA.OSX.Spigot.1.r, \Users\my-username\Library\Application Support\Spigot, 00000000000000000000000000000000, 1479 days 4 hours 33 mins 36 secs
OS: macOS 12.2.1 (21D62)
Agent version: 9.5.0.159
IP address: IP-address-here (192.168.0.136)
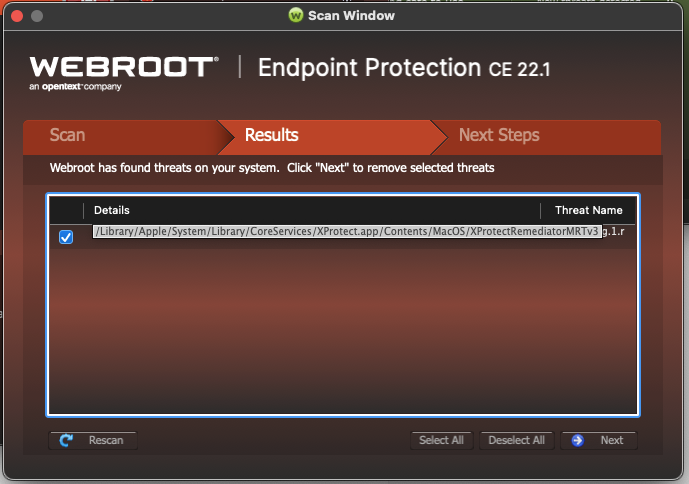
It looks like that Webroot hasn’t updated for MacOS 12.3 yet? And this is a false positive?
Hello
I would recommend getting in contact with Webroot Support and submitting a False Positive ticket with this problem. Support will be able to sort it out.
Webroot Support:
Call 1-866-612-4227
Note: When submitting a Support Ticket, Please wait for a response from Support. Putting in another Support Ticket on this problem before Support responses will put your first Support Ticket at the end of the queue.
HTH,
Dave
I got answers from support. First, they said my Mac was infected. But when I pointed out some false info, then they admitted a false positive. But haven’t got any other update yet, so my Webroot is still giving out warning :D
Having the same issue. Their support is saying that global allowlists don’t work on Mac. Is that correct?
They say I need to put the machine into Unmanaged, then on each device, manually add this file to the allowlist and run the scan again.
That seem ridiculous?
Having the same issue. Their support is saying that global allowlists don’t work on Mac. Is that correct?
They say I need to put the machine into Unmanaged, then on each device, manually add this file to the allowlist and run the scan again.
That seem ridiculous?
Hello
The problem is that Apple’s MRTs have some similarities with the malicious files we often encounter and so sometimes our system can pick them up as dangerous. Kind of annoying, I know.
So we have a planned fix coming for MRT false positive in an upcoming release and a fix to improve allow lists in another subsequent upcoming release. We’re aware of these issues and are trying our best to prioritize and release them, so for now the work around is the best option and just know that we are working towards resolving this issue actively.
I have exactly the same issue after updating to 12.3 on an M1 Mac. I have tried to use the workaround but the Allow List is greyed out?
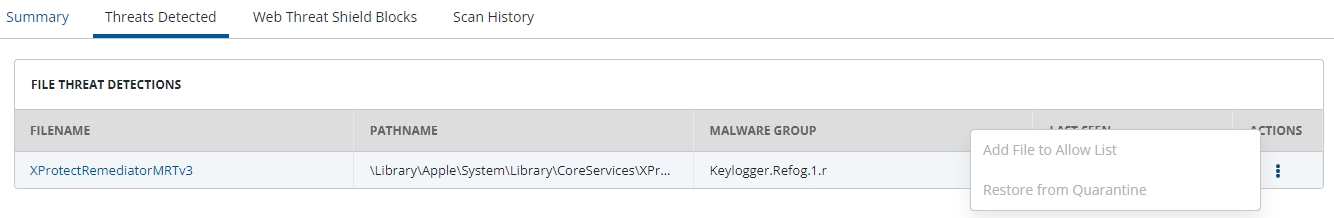
Does this mean we have to move thousands of machines that we have to the “unmanaged policy” and then go to each individual computer and add the file to the allow list???
New exclusions for the MRT v3 have been created for the next release of Malware definitions. Our team will be having a conversation today to discuss what next steps are and when we can release these new exclusions. Hopefully this will mitigate problems with MRT v3 while we can implement further long term fixes. I will update you on the timeline for that definitions release when I know it.
We need a method to do this through the console as it’s unrealistic to have to set thousands of systems to “unmanaged’ and manually run a scan, deselect the false positive detection, wash, rinse and repeat.
What’s the purpose of the console if we’re unable to perform the management tasks needed? And why has there been such a massive lack of improvement in all aspects of the product?
Something has to give before Webroot loses more MSP clients to other vendors.
John
Is there any update on when the new definitions will be released?
Got the threat of the MRT v3 last night after downloading the Apple updates earlier in the week. After reading the threads I decided to hold tight until you came up with a fix. Per Chad’s email the definitions were posted today. I logged on my computer at around 3:30 pacific time and rescanned. The service still shows it as a threat. What is my next step. I do have the option to allow it.
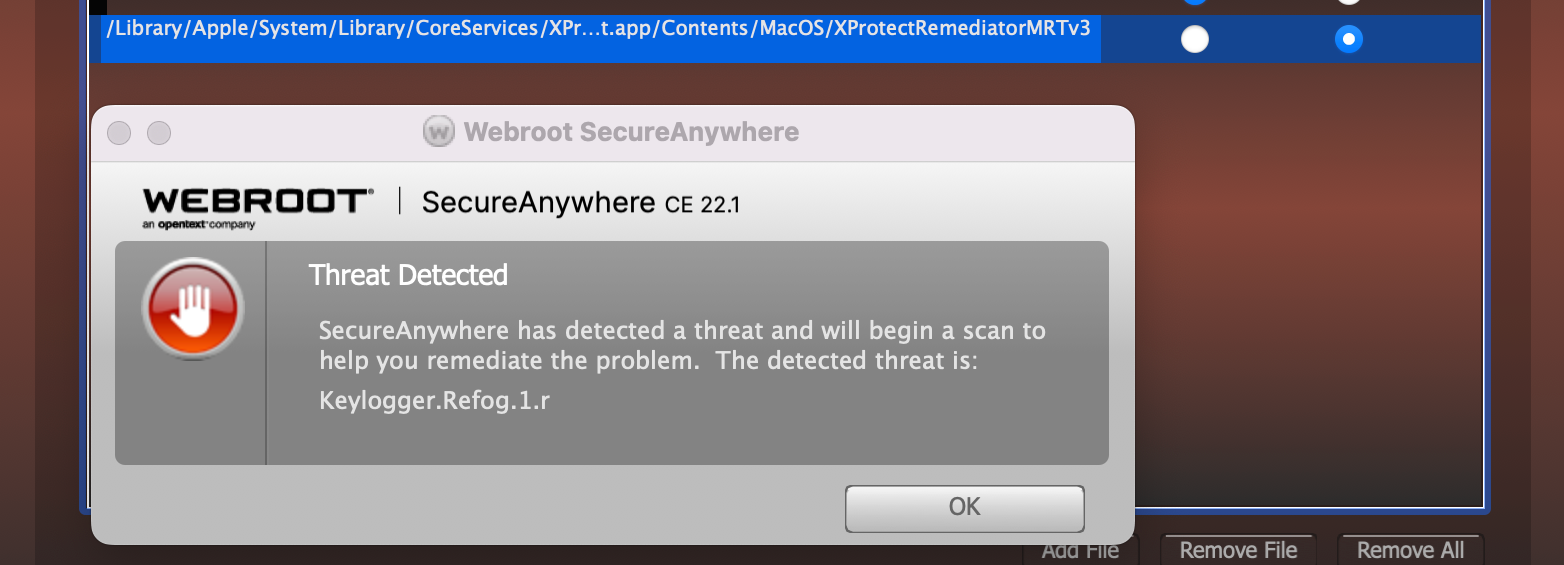
Here to report I am still seeing this flagged as of 03/19. Just to be sure I am okay to set this to the allow list correct?
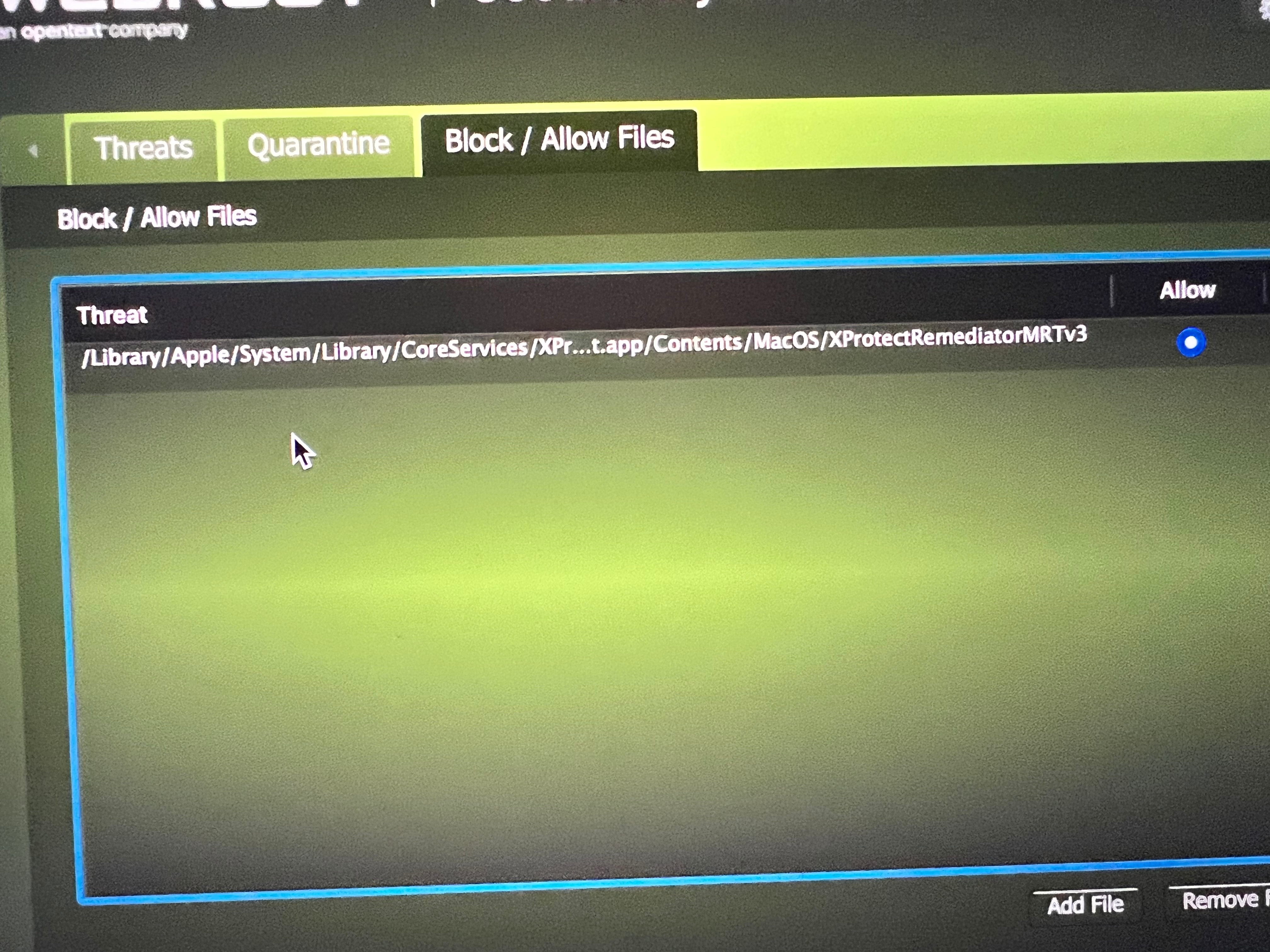
Now that the latest definitions are posted. MDT which should include an exclusion for the MRT v3 Keylogger issue.
Latest definitions as of noon PT Sunday are still flagging this MRTv3 file as a keylogger
Not sure why I had do spend several hours sweating this topic this morning when Webroot understood it days ago. Keyloggers scare the shit out of people and should be a very high priority issue to solve, or in this case flag as a false positive. Why did your team sit on it?
Latest definitions as of noon PT Sunday are still flagging this MRTv3 file as a keylogger
Not sure why I had do spend several hours sweating this topic this morning when Webroot understood it days ago. Keyloggers scare the shit out of people and should be a very high priority issue to solve, or in this case flag as a false positive. Why did your team sit on it?
I agree - if Webroot would just communicate to the customer life would be easier. Just think of the tens of thousands of hours wasted because Web Root won’t proactively update the customer - a simple message could be pushed out to all users via same system that deploys new threat definitions.
Here to report I am still seeing this flagged as of 03/19. Just to be sure I am okay to set this to the allow list correct?

It is still broken on Sunday afternoon
As of 3/21/2022 - This is still an issue for many of my clientele.
I came here this morning because last night I was given the same error/warning.
Rebooted the system (which should have loaded the latest Webroot updates) and ran a sweep last night. I am still “infected”.
Good to know I’m really not and don’t have anything to worry about, but it’s still unnerving.
We have a few macOS machines that are still reporting this as an alert even after the supposed updated definitions. Is there any action we need to take to get this to update? Thanks.
Thank you.
Webroot - if you are going to take days to weeks to fix this, at least post instructions on how to temporarily clear this without turning off or uninstalling your software.
I think the entire MSP/MSSP community and partners deserve some sort of explanation as to why the entire product portfolio, support and partnerships in general are taking a nosedive.
Can we get some responses please?
We have thousands and thousands of endpoints with you and these sorts of things makes us want to go elsewhere.
Thanks
John
Hello everyone!
Sorry about the continued issues and I will ping some Webroot Staff.
Has anyone contacted Webroot support?
For Consumers:
Webroot Support:
Call 1-866-612-4227
For Business:
CALL US
1-866-254-8400
Sorry again.
No account yet? Create an account
Enter your username or e-mail address. We'll send you an e-mail with instructions to reset your password.