Like I said I still do have some questions:
- Logfile:There are some informations in the WRLOG.log which I don't understand or can't relate to anything: [524832/0000001D] [(null)]; [Flags: 00001000.0]; Type: 3 (4661)
- Rollback/Journaling: Where can I find out what applications and which application objects are getting journaled? And can you manually do a rollback or extract data from the journal?
- Monitoring: How long are unknown processes monitored? Let's say I've got a self-made script which won't exist in the wild; will every change by this script get monitored forever(without whitlisting it)?
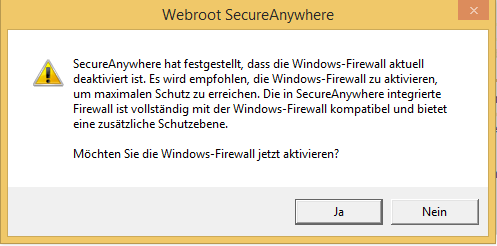
- Firewall: Does the WSA firewall only work in combination with the Windows firewall? And is the firewall compatible with a proxy server?
- From what I read WSA also includes a webfilter; can we manually block websites?
- During my test I noticed that the log file is incomplete(webconsole): I have downloaded the EICAR testfile and also created a "bad" override for an application. Both were blocked on the client but didn't show up in the webconsole. Should I open a support ticket for this case?
- I have already asked Nic this question: As WSA only secures the client where it's installed; shall we only care about our own clients or should we also prevent passing malware to other people (like sending it via email or putting it on USB)?
General questions:
- Is there a documentation available for WSA?
- Does Webroot have a KB with a detailed analaysis on threats? (like Sophos KB)
Thank you very much for your help! 🙂