With 2023 around the corner, we’ve seen yet another eventful year for the threat landscape and malware continues to be center stage in the threats posed towards individuals, businesses, and governments. The infosec industry continues the struggle of the perpetual cat and mouse game tactics that haven’t really stopped since cybercriminals first started decades ago. This absolutely accelerated into overdrive the past 9 years with the mainstream adoption of ransomware payloads and cryptocurrency facilitating payments.
If you’ve seen our writeup of Blackhat 2022, the keynote speakers noted that in 25 years of doing hacking conferences, we still don’t have a handle on what’s going on, and the surface area of attack is only growing so we all expect it to get worse.
The ransomware double extortion tactic continues to be a match made in heaven for criminals and absolute hell for victims. Every major ransomware campaign has been utilizing a Tor leak site for data exfiltrated with the intention of publishing the data in the most embarrassing and damaging way if the ransom is not paid. Some groups will threaten to leak data even if the victim attempts to work with ransom negotiation services that are typically included in cybersecurity insurance. As a result, many organizations are shifting from relying on cyber insurance policies to increasing the strength of their layered defenses in order to be more resilient against ransomware attacks.
Ransom payments have also been increasing at a much higher rate than inflation. The peak average ransom payment was above $300,000 earlier this year, it looks to have leveled off to around $225,000 now. While this may sound like a good trend in the short term, if we look back to last year's nastiest malware writeup, “The good news (I guess) is that last year’s average ransom payment of $200,000 was its peak, and today’s average is just below $150,000.” Looking back even further to this time in 2019 the average ransom payment was below $40,000. This certainly does look like an obvious and very unsettling trend.
Bad actors do seem to have finally found their sweet spot of small to medium sized business (SMB) targets. While there are major headlines of large-scale attacks on massive 10k+ employee companies with seven figure ransom demands, these are few and far between comparatively. It’s a better return on investment for ransomware groups to target the smaller environments that are easier to compromise, and they seem to have figured this out. Managed Service Providers (MSP) that provide IT services to SMBs are the ultra-juicy targets.
Phishing continues to dominate in all cybercriminal use cases, whether it's for identity theft and fraud, or for user compromise as the first step in a full environment breach that ultimately leads to ransomware. A trend that we noticed in previous years was that after the holiday season in the new year, phishing would take a back seat in the first few months of the calendar year and would peak later in May and December.
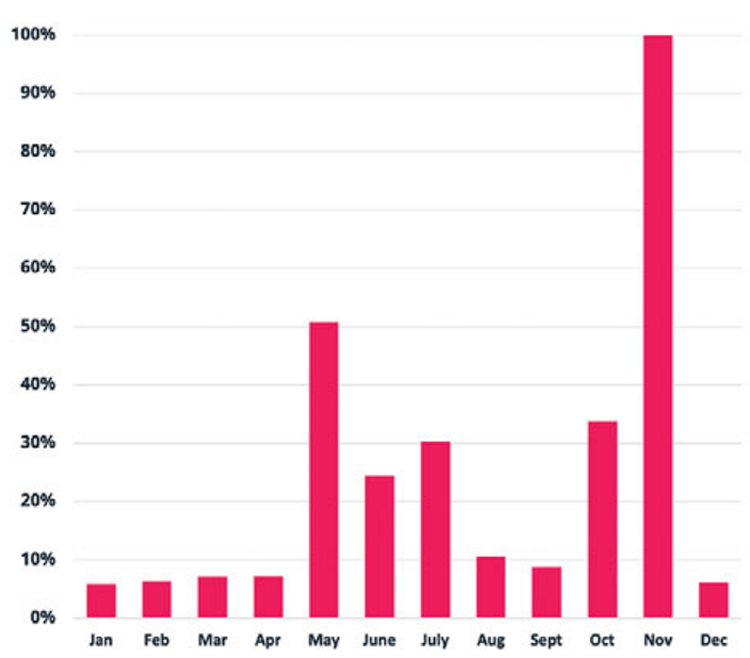
This break early in the year was widely considered the “hacker holiday” and is typically when bad actors would take a vacation and spend their holiday earnings. However, this year, the trend looks to have ended and we saw an almost 1100% increase in phishing in the first 4 months of 2022 compared to the same period in 2021. This is very concerning, and we hope it’s not the new normal, but we’ll have to see what happens next year to confirm if this is a new trend.
It’s not all bad news as earlier this year we saw the most we’ve seen out of law enforcement agencies striking back against ransomware gangs. REvil, who has been featured on our Nastiest Malware list consistently since we’ve been doing it, got hit the hardest. At the beginning of 2022, Russian authorities arrested members of the REvil gang and seized their computers and other assets. The REvil shutdown represents a positive sign for 2022 as law enforcement agencies develop more robust capabilities to arrest, prosecute and incarcerate ransomware gangs.
That’s the good news. Unfortunately, the Ransomware as a Service (RaaS) business model is thriving. Ransomware gangs such as DarkSide and REvil were taken down, only to resurface later in a reduced or rebranded form. This is simply too common in the threat landscape and celebrating any bad actor’s group shutdown usually leads to embarrassment when they rear their ugly heads again. There’s simply so much money to be made from ransomware that there are always others willing to risk imprisonment for a lucrative payday. The RaaS model also reduces the risk for ransomware coders and leaders at the top of the ransomware gangs. Those individuals still aren’t being caught or prosecuted, only the ransomware distributors and affiliates lower in the hierarchy.
With that hefty background information of this year's threat landscape happenings, let's dig into this year's Nastiest Malware. While the list below may define payloads into different categories of malware, note that many of these bad actor groups contract work from others. This will allow each group to specialize in their respective payload and perfect it.

Emotet
If there was ever a malware campaign that was contracted with so many other bad actor groups and more resilient to shutdowns, it would be Emotet. This malware is no stranger to our Nastiest Malware lists and last year when we celebrated its shutdown, it came back from the grave to renew our fears of zombie-like malware that just won't die.
At its core, it is the most successful botnet in existence. Its job is to send malspam campaigns out to billions of emails a day. Macros are the typical infection vector requiring the victim to “enable content” in the office document attachment. Microsoft has flip-flopped recently on whether they want to ban macros from showing by default or not on office documents. We’d sure wish they’d make up their mind and just ban them please. Even if macros are banned in office documents, we’ve seen some pivots into the adoption of .lnk (shortcut) file replacements in the infection chain instead of VB Macros in an excel file. The scam changes the icon to something that looks like a document (a tactic we’ve not seen for ages).
Emotet is just the first stage, and its job is to create a foothold on the victim's computer for follow-up malware that will then move laterally and compromise the rest of the environment before bringing in the final payload of ransomware. Emotet is so effective and resilient, it is crowned our king of nastiest malware.

Lockbit
This year's most prolific and successful ransomware group is LockBit. They’ve been around for about three years now as a RaaS group and the new trend they’ve evolved into this year is TRIPLE EXTORTION. Back in June, Enrust was the victim of a ransomware attack by Lockbit
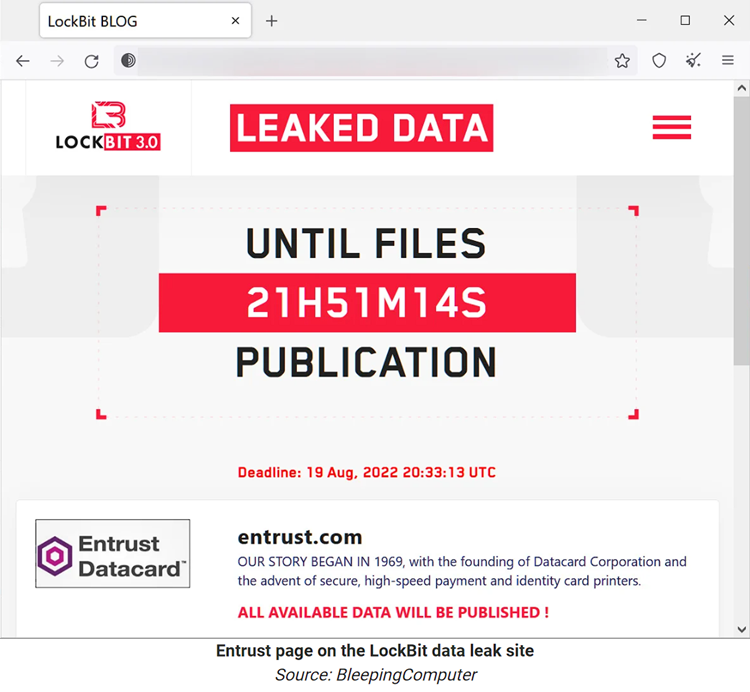
Lockbit threatened to release all the data compromised by the attack and Entrust used DDOS against Lockbit to delay/stop this leak of data. This caused quite a rumble with Lockbit and in a recent post reported that they are now looking to operate DDOS and create triple extortion: encryption + data leak + DDOS “because I have felt the power of DDOS”
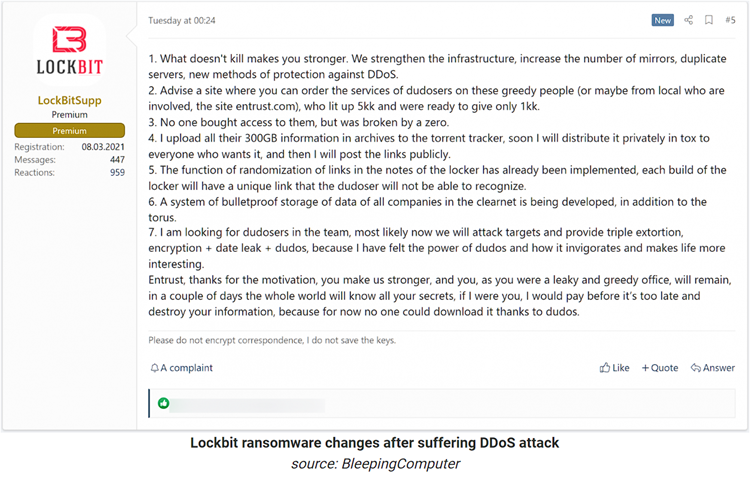
If that wasn’t nasty enough, Lockbit is so hellbent on being the most dangerous and resilient ransomware payload out there, that they also now have a bug bounty program that pays out $1k-$1M.
Web Site Bugs: XSS vulnerabilities, mysql injections, getting a shell to the site and more, will be paid depending on the severity of the bug, the main direction is to get a decryptor through bugs web site, as well as access to the history of correspondence with encrypted companies.
Locker Bugs: Any errors during encryption by lockers that lead to corrupted files or to the possibility of decrypting files without getting a decryptor.
Brilliant ideas: We pay for ideas, please write us how to improve our site and our software, the best ideas will be paid. What is so interesting about our competitors that we don't have?
Doxing: We pay exactly one million dollars, no more and no less, for doxing the affiliate program boss. Whether you're an FBI agent or a very clever hacker who knows how to find anyone, you can write us a TOX messenger, give us your boss's name, and get $1 million in bitcoin or monero for it.
TOX messenger: Vulnerabilities of TOX messenger that allow you to intercept correspondence, run malware, determine the IP address of the interlocutorand other interesting vulnerabilities.
Tor network: Any vulnerabilities which help to get the IP address of the server where the site is installed on the onion domain, as well as getting root access to our servers, followed by a database dump and onion domains.
Lockbit is also the only ransomware that takes payments in Bitcoin, Monero, and Zcash. Monero and Zcash are privacy coins that do not utilize a private ledger and therefore 100% fungible. This is basically perfect for criminal use cases in evasion and laundering as there simply isn’t anything any government entity can do to stop this. If exchanges continue to make these coins available for purchase, they won't be going anywhere, and more ransomware groups will adopt them in conjunction with Bitcoin.

Conti
Conti is a big name in the ransomware scene and has been on our Nastiest Malware radar for quite some time. They’ve had a wild ride this past year to put it mildly. Earlier in February when Russia invaded Ukraine, Conti released a statement on their leak site with their support of the Russian government.
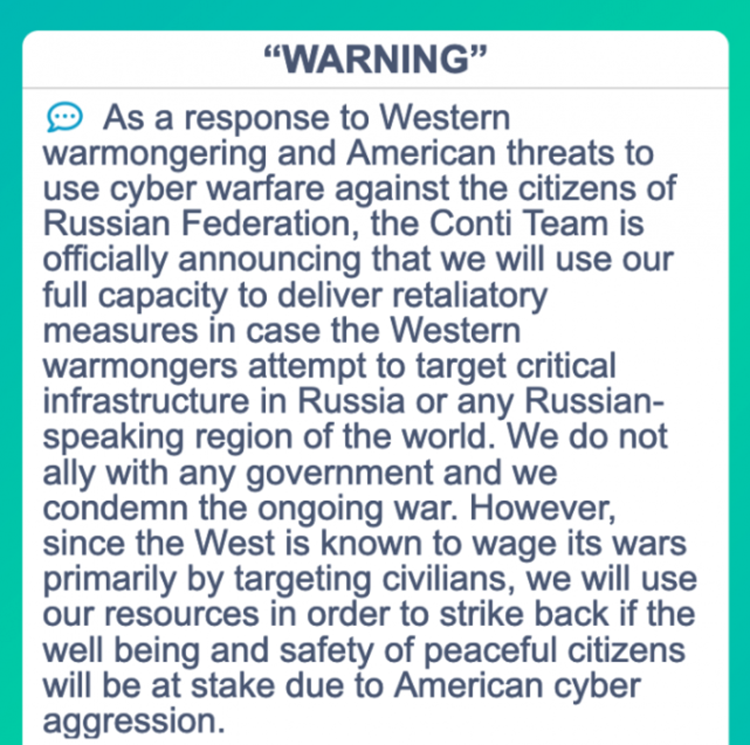
After this a twitter account, “Conti leaks” leaked all of their internal chats dating back almost two years. This resulted in the dismantling of their leak site and command and control servers, presumably by the Conti group. However, they are not gone, far from it. They decided to dismantle operations and instead rebrand into many other different operations. If you’ve heard of HelloKitty, AvosLocker, Hive, BlackCat, and BlackByte just know that Conti group affiliates are now behind those ransomware groups. Ransomware strains are always the final payload in an environment breach. It’s only after the cybercriminals have gained access to everything they want and made sure that their payload will be most damaging that it is deployed. While typically deployed from RDP, it's not usually brute-forced from unsecured RDP. Most often the credentials are grabbed or phished elsewhere, like from info stealing trojans such as Trickbot or Qbot.
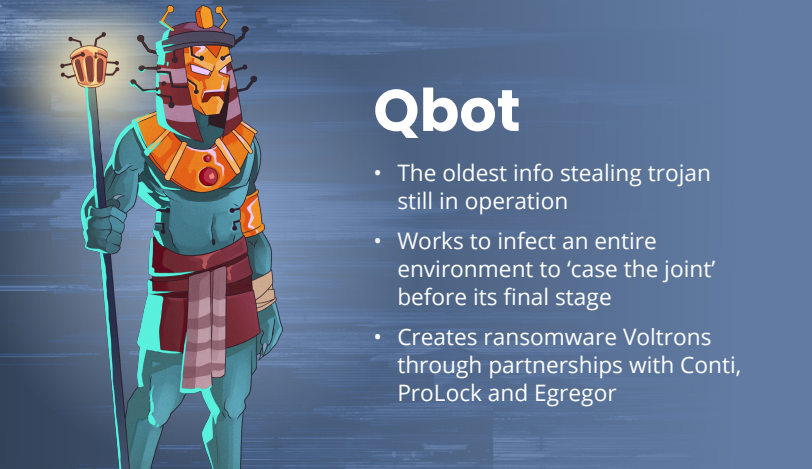
Qbot
Qbot (AKA Qakbot) is probably the oldest infostealing trojan still receiving updates today. Qakbot has been seen dropped by emotet, but also through it’s own malspam campaigns with attachments and links to compromised websites. Its job is similar to Trickbot and Dridex to move throughout the network and infect the entire environment. To “case the joint” and allow access to as much data as possible to exfiltrate for extortion and to prepare for the final stage of ransomware payloads. Since ransomware is the top-tier strategy to monetize an infected environment, Qbot has been seen teaming up with many big-name Ransomware groups like Conti, ProLock and Egregor.

Valyria
Valyria is yet another strain of a used-to-be banking trojan that turned into malspam botnet with email attachments into malicious scripts that start the infection chain typically resulting in ransomware. Valyria has also been seen partnering with Emotet (who hasn’t at this point). The tricky part about Valyria is the complexity of the components. There are numerous parts of the dropper even on a single system from the same attachment including a multitude of encrypted and unique functions that were initially designed to begin data collection. With this design, they would often evade detection by the sheer number of pieces all designed to load the next stage of malware. One macro might create scheduled tasks, services to run single commands, process threads, injection methods, debugger evasion and mouse and keyboard hooks and suspended processes to later recall. Though most of the pieces all fit together by pointing at the same or similar address to pull down payloads that would then be run reflectively thus increasing the complexity of detection and remediation.

CobaltStrike/Brute Ratel
Cobalt Strike is a pen testing tool designed by white hats. Its purpose is to help red teams simulate attacks so hackers can infiltrate an environment, determine its security gaps and make the appropriate changes. There are several very powerful and useful features in this tool like process injection, privilege escalation, credential and hash harvesting, network enumeration, lateral movement and more.
All these are attractive to hackers, so it’s not surprising that we’ve seen Cobalt Strike and Brute Ratel used by the bad guys OFTEN. It’s unique for us to list a tool for white hats on among our Nastiest Malware, but this tool is easy to use for scalable, customized attacks. It’s no wonder so many threat actors are adopting it as one of the tools in their arsenal. This is one of the most common trends that we’ve seen recently, and we expect it to continue.
These tools are specifically designed to evade defenses and allow for infiltration but somehow don’t get the same categorization as malware as a service even though they clearly are.
Honorable mentions
Shlayer
Mac malware doesn’t usually get that much attention these days, but Shlayer is changing that this year. Commonly referred to as “adload” Shlayer will disguise itself as a fake Adobe Flash Player or fake MacOS update popups on hijacked domains or clones of legitimate sites. Shlayer also managed to get their payloads through Apple’s automated notarizing process, effectively certifying themselves through the macOS Gatekeeper. After tricking a victim to installing it, it will use proxy software to analyze and modify HTTPS traffic to inject ads and malicious scripts into visited sites.

XMRig – yet another “legitimate tool” for legitimate miners to mine the popular cryptocurrency Monero. However, MUCH of the mining by XMR rig is illegitimate and yields ill-gotten gains for criminals. Monero has proven useful for criminals not just because it’s private. It also has a proof-of-work mining system that maintains an ASIC resistance. Most cryptocurrencies use a proof-of-work mining system, but the algorithm used to mine them can be worked by a specific chip (ASIC) designed to hash that algorithm much more efficiently than the average personal computer.
In this sense, Monero has created a niche for itself with a development team that maintains it will continually alter the Monero algorithm to make sure that it stays ASIC-resistant. This means Monero can be mined profitably with consumer-grade CPUs, sparking yet another trend among criminals of generating money from victims without ever delivering “malware” to their systems. Choosing to target the CPU in a breach and monetize it is a great alternative if the hackers believe that ransomware wouldn’t be a great option. Cryptomining is instant profitability and as long as the victims aren’t made aware of the miners, the profits are indefinite.


How to stay safe
It’s time to sharpen your stakes, polish your pitchforks and learn how to keep safe from monstrous malware. With attackers becoming more sophisticated every year, it’s important to have a multi-layered protection strategy.

Here are some tips from our experts
Businesses
- Lock down Remote Desktop Protocols (RDP).
- Use RDP solutions that encrypt data and use multi-factor authentication. This needed increase in security protects against vulnerabilities when remoting into other machines. Make sure you are aware of all the remote desktop software being used as criminals are now installing legitimate remote desktop tools to backdoor your environments while also avoiding detection.
- Educate end users.
- Preventing attacks starts with stronger awareness among end users. Running regular cybersecurity awareness trainings and phishing simulations keeps data safe and secure. Also, make sure employees know when and how to report a suspicious message.
- Install reputable cybersecurity software.
- Choose a solution that uses real-time, global threat intelligence and machine learning to stop threats. Look for protection with multi-layered shielding to detect and prevent attacks at numerous different attack stages.
- Set up a strong backup and disaster recovery plan.
- With hybrid work with us for the long haul, businesses can’t afford to go without a strong backup. Test backups regularly and set alerts so admins can easily see if something’s amiss.
Individual Users
- Develop a healthy dose of suspicion toward messages.
- Treat your emails like the same way you’d treat a graveyard in a horror movie. Don’t click on links or attachments in emails. Be suspicious of any emails, texts, phone calls or social media messages that ask for personal info.
- Protect your devices with antivirus and a VPN.
- Be sure to secure not just computers, but smartphones and tablets, too. And when you ditch an old device, be sure to wipe it first.
- Keep your antivirus software and other apps up to date.
- Hackers use outdated software and operating systems to get malware onto your system and steal from you. Install updates.
- Use a secure cloud backup.
- We recommend using both an online backup that stores your data in an encrypted format and a physical backup drive that you unplug when not in use.
- Create strong, unique passwords (and don’t share them).
- Length = Strength. Use passphrases to increase the characters of passwords and defend against brute force
- You can use a password manager to help you create and store good passwords. That way, you don’t have to remember them all or write them down.
- If a file you downloaded asks you to enable macros, DON’T DO IT.
- This is a strong telltale sign that the file is infected with malicious code. Even though macros have legitimate uses, they are extremely rare in a normal home user context.
- We’ve seen some adoption of .lnk file replacements in the infection chain instead of VB Macros in an xcel file. The scam is changing the icon to something that looks like a document.
Make sure to check out our infographic attached below!















