As mentioned in a previous post, cybersecurity experts widely believe the SolarWinds attack will inspire other supply chain attacks with similarly devastating consequences for all types of businesses. In that initial statement on our Community page, we promised to expand on our tips for protecting your business or clients from the inevitable fallout of future attacks.
That protection starts with contextual, actionable threat intelligence. Maybe it’s not the flashiest of defense tactics, but the basics still matter. While other security vendors may have marked SolarWind's Orion updates as coming from a trusted partner, the right threat intelligence feeds could have prevented further communication with the C2 server used in the attack.
In the case of the Webroot BrightCloud Threat Intelligence platform, an IP address involved in the attack had been associated with a botnet and categorized as high-risk in the summer of last year Properly configured, our security tools would have blocked communication with that command and control server. This may have helped to contain the knock-on effects of the breach.
Threat Intelligence platform, an IP address involved in the attack had been associated with a botnet and categorized as high-risk in the summer of last year Properly configured, our security tools would have blocked communication with that command and control server. This may have helped to contain the knock-on effects of the breach.
This demonstrates how the different elements of a defense-in-depth strategy can help to reinforce an organization's defenses even when one layer is unexpectedly overcome. That’s why our first piece of advice for defending against the next supply chain attack focuses on basic threat intelligence.
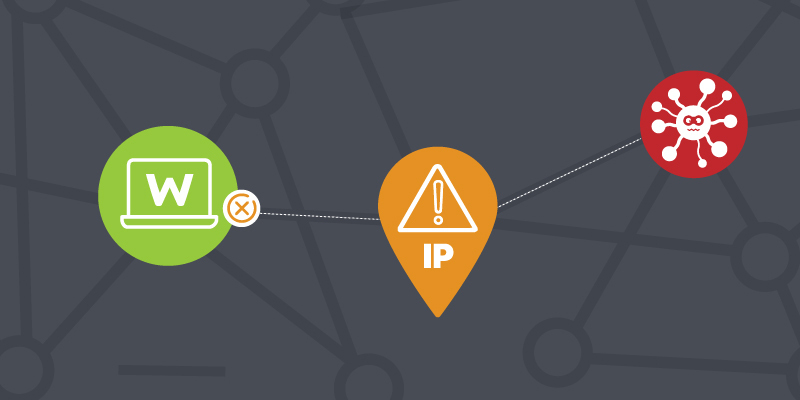
Use security technology that includes threat intelligence for URLs, domains and IP addresses
The fundamental elements of tactical threat intelligence still play a critical role in a layered cybersecurity approach.
By fundamental elements we mean tactical threat intelligence that focuses on the latest methods threat actors use to execute an attack. These include indicators of compromise (IOCs) like IP addresses, URLs, system logs and files that can help detect attacks. This type of threat intelligence is most often deployed in network and security devices like firewalls, SIEMs, TIPs and other tools, and is usually set to apply policy-based settings within these devices based on intelligence criteria.
Recent attacks show that these fundamental tactical threat intelligence elements remain critical. While web filtering and URL classification, IP reputation and file detection and reputation may seem less exciting than threat actor profiles and takedown services, they are core threat intelligence elements for stopping attacks.
These IOCs – files, IPs, URLs – are commonly relied on by threat actors and play a consistent role in malicious campaigns. Having tactical intelligence on these items is one big step security and technology providers can take to ensure their end users are better protected.
Like any single layer of protection, tactical threat intelligence is a necessary but on its own, an insufficient tool for fighting advanced attacks. Even when the right tools are in place, they must be configured properly. Too often, for convenience sake or some other reason, best practices for configurations are ignored.
We’ll explore that topic a bit more our next post…