Microsoft Security Advisory (2953095)
Vulnerability in Microsoft Word Could Allow Remote Code Execution
Published: Monday, March 24, 2014Version: 1.0
General Information
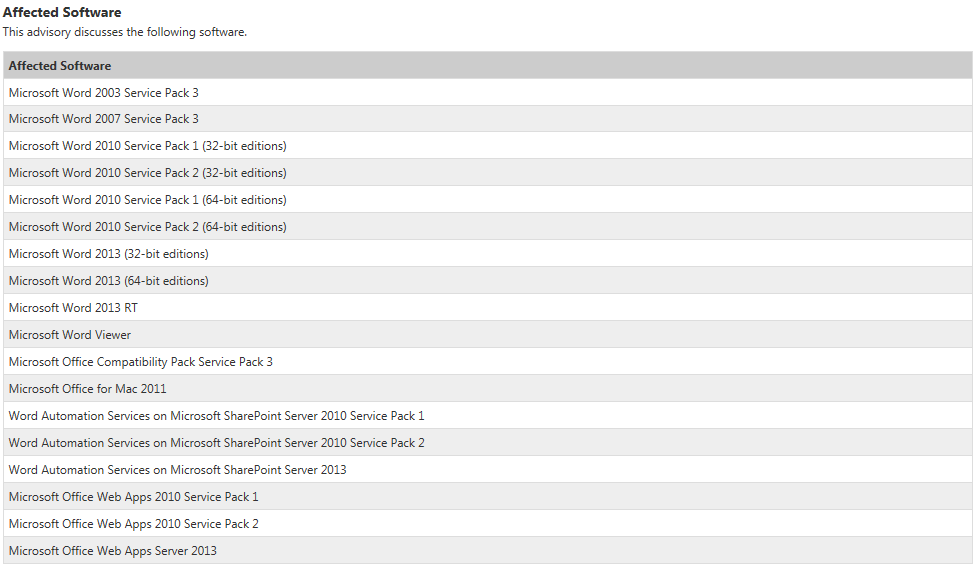
Executive SummaryMicrosoft is aware of a vulnerability affecting supported versions of Microsoft Word. At this time, we are aware of limited, targeted attacks directed at Microsoft Word 2010. The vulnerability could allow remote code execution if a user opens a specially crafted RTF file using an affected version of Microsoft Word, or previews or opens a specially crafted RTF email message in Microsoft Outlook while using Microsoft Word as the email viewer. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights. Applying the Microsoft Fix it solution, "Disable opening RTF content in Microsoft Word," prevents the exploitation of this issue through Microsoft Word. See the Suggested Actions section of this advisory for more information.The vulnerability is a remote code execution vulnerability. The issue is caused when Microsoft Word parses specially crafted RTF-formatted data causing system memory to become corrupted in such a way that an attacker could execute arbitrary code. The vulnerability could be exploited through Microsoft Outlook only when using Microsoft Word as the email viewer. Note that by default, Microsoft Word is the email reader in Microsoft Outlook 2007, Microsoft Outlook 2010, and Microsoft Outlook 2013.
On completion of investigation for this vulnerability, Microsoft will take the appropriate action to protect our customers, which may include providing a solution through our monthly security update release process, or an out-of-cycle security update, depending on customer needs.
We are actively working with partners in our Microsoft Active Protections Program (MAPP) to offer information that they can use to provide additional protections to customers. For information about protections released by MAPP partners, see MAPP Partners with Updated Protections.
Microsoft continues to encourage customers to follow the guidance in the Microsoft Safety & Security Center of enabling a firewall, applying all software updates, and installing antimalware software.
Full Article