Now presenting "flash-install.ru", which is listed in a .ru Whois registry as having been "created 2014.03.05".
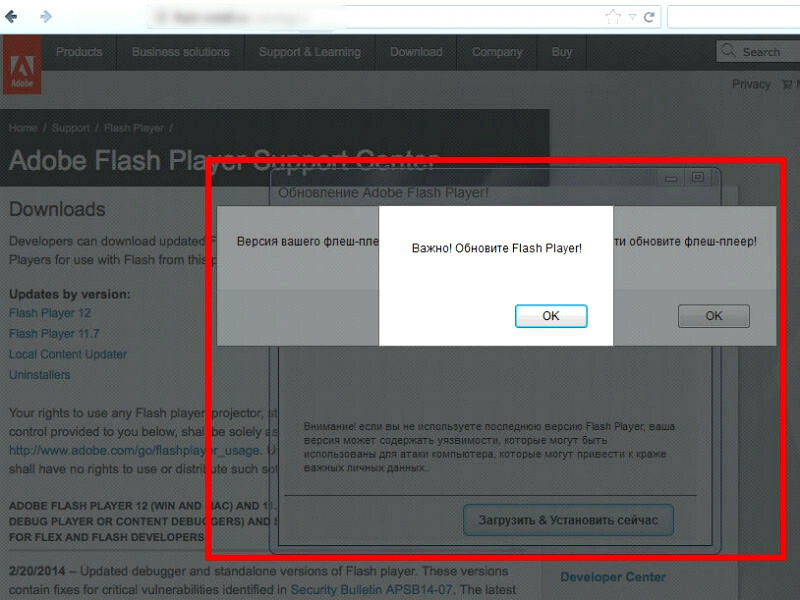
The no-doubt somewhat off-kilter Google Translation of the boxes reads as follows:
- Update available for Mozilla Firefox:
- Flash Player 12.0.0.44
- It is recommended to update Flash Player as soon as possible.
- Attention! if you are not using the latest version of Flash Player, your version may contain vulnerabilities that could be used to attack your computer, which can lead to theft of important personal data.
From there, additional URLs and files are called out to and keep this show on the road. The Malwr sandbox report makes for good reading, and lists the following http requests:
mrfc.by
jiojhijo.cf
coca.su:15170
on the Dropped Files tab (of which there are many, though the ones showing on VirusTotal are flagged as "Probably harmless! There are strong indicators suggesting that this file is safe to use") we can see a file called "Minerd.exe", with an MD5 of:
ea5c563db06d96b90141698afd27f2fc
The VirusTotal report for that one pegs it at 36 / 50, and is - as the name suggests - a Bitcoin mining program. Malwarebytes detects the initial file - installer.exe - as Trojan.Crypt.NKN. We also detect the "Minerd" file as PUP.BitCoinMiner.
We've looked at fake Flash installs before - and whether desktop-based SMS antics or phony Youtube video updates, it pays togo direct to the source when prompted to update something on your PC.
It's the only way to be sure.
Source