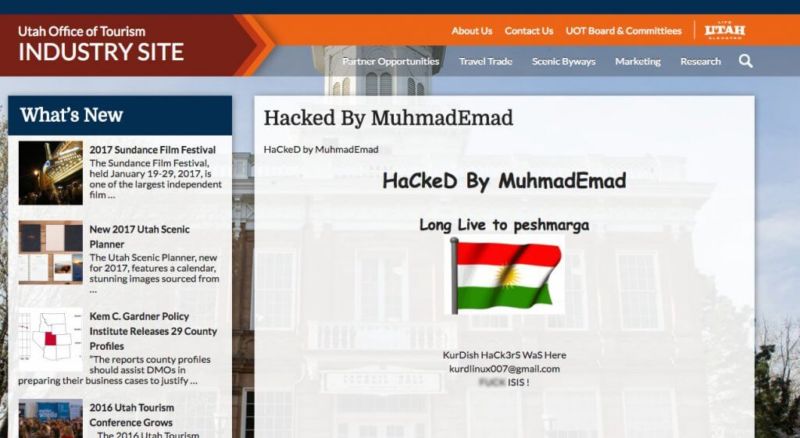
February 2, 2017 By Pierluigi Paganini
A new dangerous Zero-day Content Injection vulnerability has been discovered in the WordPress CMS, it affects the WordPress REST API.
A new dangerous vulnerability has been discovered in the WordPress CMS, it is a zero-day content injection flaw in the WordPress REST API.
The vulnerability discovered by a security researcher at firm Sucuri could be exploited by an unauthenticated attacker to inject malicious content as well as for privilege escalation.
The attacker could exploit the zero-day content injection vulnerability to modify posts, pages, as well any other content.
Experts from Sucuri have worked with the WordPress development team that fixed the zero-day content injection vulnerability in the last release 4.7.2.
Full Article