Stream the Webinar on demand!
Check out our Nastiest Malware infographic attached below!
We've been doing the Nastiest Malware series for over 5 years now and in that time, we have seen a steady increase in the number and sophistication of malware attacks. Ransomware has been the most prevalent type of malware, with cybercriminals increasingly targeting businesses and organizations. Criminal actors in the Ransomware sector have come up with new “business models” and ransomware-as-a-service (RaaS) is dominating. Elite Ransomware authors appear to have concluded that profit sharing and risk mitigation are top contributors to their consistent success and reliable evasion from authorities. Malware payloads are becoming more sophisticated and difficult to detect, and we expect their tactics to be ever evolving.
Reflecting on the past five years of the malware landscape offers invaluable insights into the evolution of cyber threats.
- In 2019, the most prevalent malware was Emotet, a botnet that enabled footholds and proliferation of ransomware partners. Other notable malware from this year included TrickBot, Ryuk ransomware, and GandCrab ransomware. Unsecured RDP was a top attack vector for infiltration and was essentially the back door left wide open.
- The COVID-19 pandemic led to a surge in malware attacks in 2020, as cybercriminals took advantage of the increased online activity. The most prevalent malware in this year was TrickBot, followed by Emotet and Ryuk ransomware. Phishing rose to new heights and dominated the landscape with new tactics revolving around the pandemic.
- The malware landscape continued to evolve in 2021, with new strains of ransomware and other malicious software emerging while some getting shut down. The most prevalent malware in this year was Conti ransomware, followed by LockBit ransomware. Cobalt strike – a Whitehat pen testing tool was abused by criminals for their operations sparked a new trend.
- The ever-increasing price of Ransomware continued in 2022, with new variants of and other malware being developed continuously. The most prevalent malware in this year was LockBit ransomware, followed by Conti ransomware. Emotet came back from the dead after being shut down in 2021 – a trend that we continue to see :(
- The Russia-Ukraine conflict has had notable repercussions on the malware landscape. The geopolitical tensions have been mirrored in cyberspace, with an uptick in cyber-espionage campaigns and targeted attacks. Both nations and their affiliated hacktivist groups, have been implicated in deploying sophisticated malware strains against each other, affecting critical infrastructure and spreading disinformation, further highlighting the evolving nature of modern warfare where digital frontlines are as active as physical ones.
Overall, the past 5 years have seen a steady increase in the number and sophistication of malware attacks. Cybercriminals are highly adaptable and will use any means necessary to achieve their goals. They are a threat to organizations of all sizes, and it is important to be prepared for their attacks. This trend is likely to continue in the years to come, as cybercriminals become more creative and resourceful in their attempts to exploit vulnerabilities in computer systems. To compound this the world’s continued reliance on software comes with evermore vulnerabilities making supply chain attacks a growing concern.
So far in 2023, the malware landscape has been relatively consistent, with the same strains of ransomware and other malware being prevalent. However, there are signs that the threat landscape is evolving, with new malware strains being developed and old strains being updated with new features. We also saw one of the biggest takedowns in history of a multinational operation led by the FBI to dismantle the Qakbot botnet. This is a welcome change to the standard doom and gloom of the cyberthreat landscape and we hope movement like this is able to continue.
As we look to the future, the stakes are sky high for the development and use of Artificial intelligence (AI) and machine learning (ML). While these topics are absolutely the current buzzwords dominating at every security conference – see our writeups of RSA 2023 and Black hat 2023, it’s for a very good reason. Artificial intelligence (AI) and machine learning (ML) are rapidly transforming the cybersecurity landscape. These technologies have the potential to be used for both good and malicious purposes.
On the one hand, AI and ML can be used to develop new and more effective ways to detect and prevent cyberattacks. For example, AI-powered anomaly detection systems can identify patterns of behavior that are indicative of a cyberattack, even when those patterns are not easily recognizable by humans. ML can also be used to train chatbots that can interact with users in a way that is indistinguishable from a human, making it more difficult for attackers to trick users into giving up their personal information or clicking on malicious links.
On the other hand, AI and ML can also be used to develop new and more sophisticated cyberattacks. For example, AI-powered malware can learn to evade traditional antivirus and anti-malware programs. ML can also be used to generate realistic-looking phishing emails that are more likely to fool users into clicking on malicious links.
The use of AI and ML in cybersecurity is a double-edged sword. These technologies have the potential to make the world a safer place, but they also have the potential to be used for malicious purposes. It is important to be aware of both the potential benefits and risks of these technologies and to take steps to mitigate the risks.
Here are some specific examples of how AI and ML are being used in cybersecurity:
- Anomaly detection: AI can be used to identify patterns of behavior that are indicative of a cyberattack, even when those patterns are not easily recognizable by humans like unusual traffic patterns on a network or unusual behavior by a user.
- Malware detection: ML can be used to train antivirus and anti-malware programs to detect new and emerging malware threats. For example, ML can be used to identify patterns in unknown malware code that are common to many different known malware families.
- Phishing detection: AI can be used to generate realistic-looking phishing emails that are more likely to fool users into clicking on malicious links. For example, AI can be used to generate emails that are tailored to the specific recipient, making them more likely to be opened. Examples of this are already being showcased at Blackhat.
The use of AI and ML in cybersecurity is still in its early stages, but it is rapidly evolving. As these technologies become more sophisticated, they will play an increasingly important role in protecting our digital world.
2023 has seen a surge in the sophistication and audacity of cybercriminal activities. Two of the most formidable weapons in a hacker's arsenal, ransomware and botnets, have reached unprecedented levels of intricacy. These attacks have left a trail of compromised systems, financial losses, and shaken confidence in digital security. As we delve into the most notorious ransomware strains of the year, it is crucial to approach with a keen sense of awareness and understanding.
Ransomware
Mainstream Ransomware, which is now 10 years old this year 🎂 has rapidly ascended the ranks to become the weapon of choice for cybercriminals seeking to monetize breaches in digital environments. Its profitability is evident in the consistent growth of the ransoms demanded and the staggering amounts cybercriminals rake in annually. What makes ransomware even more menacing is its evolution: the sinister combination of data exfiltration with encryption. This dual-threat approach ensures that even if victims have backups to restore their systems, the looming threat of their sensitive data being leaked or sold compels them to pay or face crisis communications and data compliance fines. It's a strategy so effective that every major player in the cybercrime arena is now running this scheme in their operations.
The average ransom payment has absolutely skyrocketed this year and is now rapidly approaching three quarters of a million dollars. Yes, you read that right.
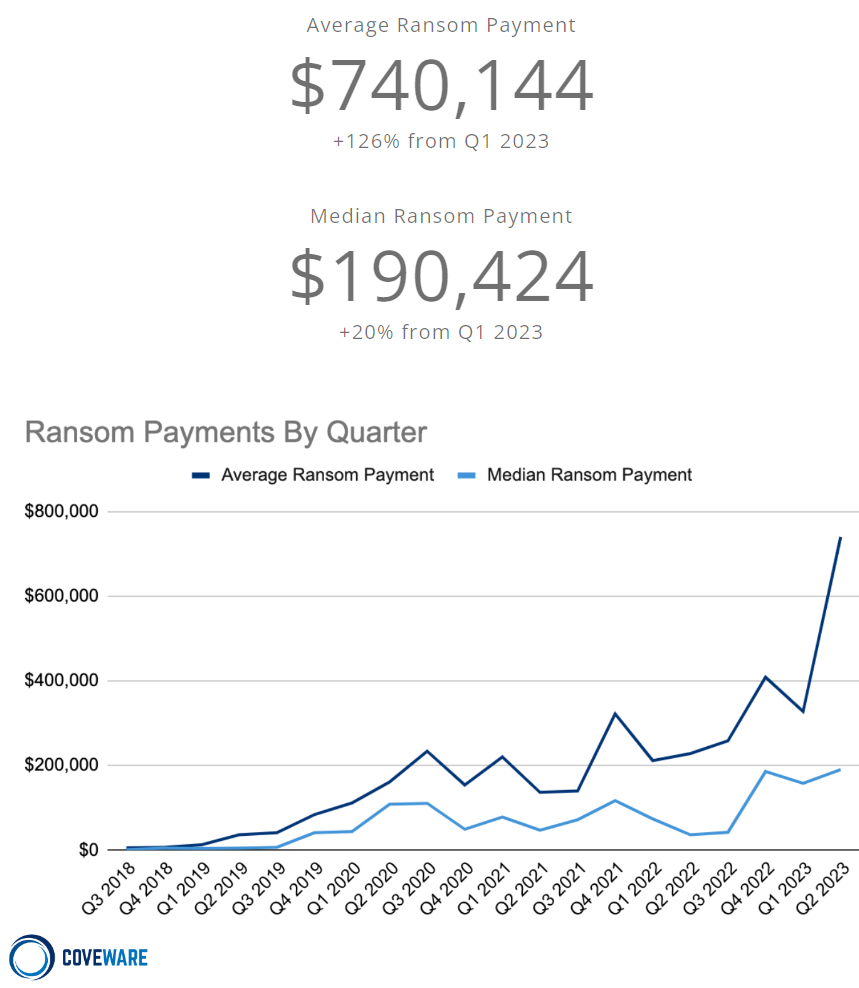
However, the reason for such a large growth in a small amount of time is likely due to the Cl0p ransomware gang earning a potential $100 Million from their MOVEit campaign. The median ransom payment has stabilized with a small quarter-over-quarter increase. However, there is good news here, the overall percentage of Ransomware attacks that resulted in victims paying has reached a RECORD LOW 34%.
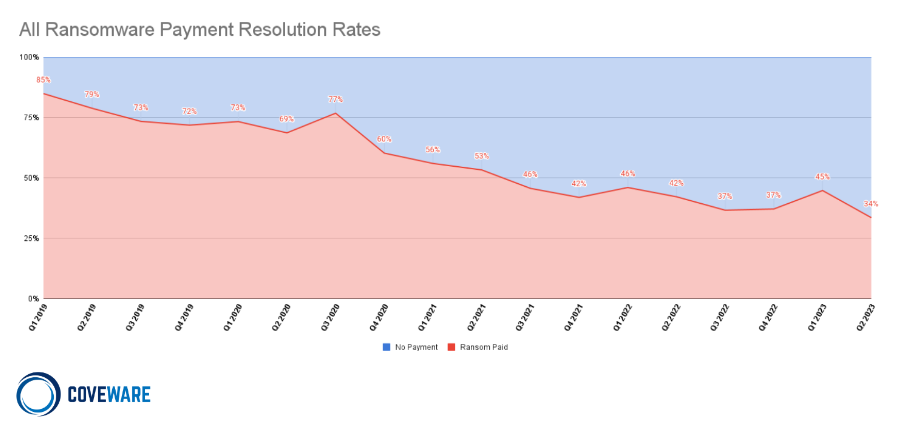
This continued decline suggests that businesses are steadily but assuredly taking the ransomware threat seriously and investing in cyber resilience to these types of attacks. In looking at the size of businesses impacted by ransomware by employee – 30% were below 100 and 66% were below 1000.
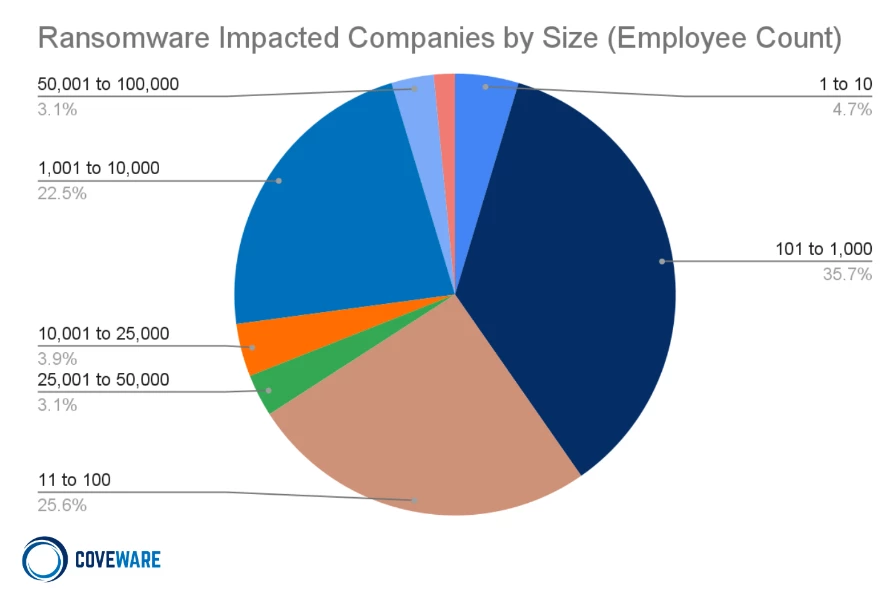
This continues the trend that we’ve noticed of large shares of the bread-and-butter campaigns targeting small to medium-sized businesses. The ease of infiltrating and spreading, quicker turnaround time for data exfiltration, decent size of cash in the bank, and overall company impact when the ransomware payload drops and encrypts, make for a devastating combo finish. Now lets dive into what our experts have picked as the top Ransomware families of 2023.
Cl0p

Cl0p is known for its sophisticated attack techniques and its ability to target a wide range of organizations. Cl0p ransomware is a RaaS (ransomware-as-a-service) platform, which means that it is available for purchase by cybercriminals. This makes it easier for cybercriminals to launch ransomware attacks, as they do not need to have the technical expertise to develop their own ransomware and just profit share with affiliates. Cl0p is often delivered via phishing emails from botnets, which are emails that appear to be from a legitimate source. These emails often contain malicious attachments or links that, when clicked and launched, will infect the entire network and prep for ransomware payload deployment. The ransom demands for Cl0p ransomware are exorbitant and some of the highest we’ve seen – especially with the MOVEit Campaign.
The Cl0p ransomware group was made famous with a series of cyberattacks that were carried out in late May 2023. The attacks targeted organizations that used the MOVEit Transfer file transfer software, which is developed by Progress Software. The Cl0p group exploited a zero-day vulnerability in MOVEit Transfer to gain access to the victim's networks. Once they had access, they would deploy ransomware to encrypt the victim's files and demand a ransom payment in exchange for the decryption key. The MOVEit campaign was a major success for the Cl0p group. They were able to infect thousands of organizations, impacting more than 60 million people and extort a combined demand price in the hundreds of millions of dollars in ransom payments.
Black Cat

BlackCat ransomware was first detected in November 2021. BlackCat is also known as ALPHV, AlphaVM, and AlphaV. BlackCat is believed to be the first ransomware-as-a-service (RaaS) written in Rust, a cross-platform language. This makes it easily customizable for different operating systems and enterprise environments. Black Cat is a successor to the REvil ransomware, which was one of the most active ransomware groups in 2021 and we covered in our Nastiest Malware 2021. BlackCat uses a triple extortion technique which Lockbit pioneered last year in our Nastiest malware 2022. Attackers identify the weakest link in a system and break in through a vulnerability there. Most of the time this is users falling for a phishing link but sometimes software vulnerabilities. Once inside, they grab the most sensitive data and exfiltrate it for the leak/extortion play. Then they encrypt the environment to cause panic shutdown operations. BlackCat is operated by ALPHV, a Russian-speaking group of cybercrime actors. BlackCat can compromise Windows- and Linux-based operating systems. BlackCat has garnered media attention when used by affiliates to compromise MGM Casinos, Seiko and hospitals and medical clinics.
The ALPHV ransomware collective operates a tiered affiliate scheme known as AffiliatePlus. When affiliates amass profits exceeding $1,500,000, they ascend to the AffiliatePlus tier. This elevated status grants them access to "Munchkin," which is ALPHV's proprietary Linux-based operating system.
Source:
vx-underground
AKIRA

Akira ransomware is a new ransomware-as-a-service (RaaS) platform that was first seen in March 2023. It is presumed to be a successor or a rebrand related to the Conti ransomware group which ran into many issues last year including chat and source code leaks which we covered on last year's nastiest malware, which was one of the most active ransomware groups in 2022. They primarily target small to medium sized businesses due to the ease and turnaround time.
The Akira ransomware group employs jQuery Terminal, a web-based JavaScript terminal emulator, to give a vintage and retro aesthetic to their data leak website. They also encrypt all files with a .AKIRA file extension
Royal

Royal ransomware is a strain that was first observed in early 2022, but they were using 3rd party ransomware payloads. Since September 2022 the group has its own brand and changes the encrypted files' extension to “.royal” They also use a unique partial encryption approach that allows the threat actor to choose a specific percentage of data in a file to encrypt which helps evade detection. The Royal ransomware group's top targets include the IT, finance, materials, healthcare, food and staples industries, and even the municipality of dallas. This group is another thought to be created from the ashes of Conti or Ryuk.
Lockbit 3.0
Lockbit was our nastiest malware last year and it’s been consistently terrifying every year since it showed its ugly tentacles. It was responsible for around one fifth of all ransomware attacks last year! It is now in its third epoch and more modular and evasive than its predecessors. The encrypted files are now also given a random 9-character file extension. The CISA agency reports that they primarily target US small to medium-sized businesses and have made almost $100 million in payments with an average ransom amount of $85,000 per victim. Interesting internal workings that contribute to their success include assuring payment by allowing affiliates to receive ransom payments before sending a cut to the core group. This is completely the opposite of other RaaS groups that require the core payload group to be paid first and then distribute the affiliates cut. Paying people to get LockBit tattoos and issuing a $1 million bounty to anyone that can successfully dox the top Banana at Lockbit. They’ve also been “trash talking” all other competitors on hacking forums and dark web marketplaces. Recently Lockbit reindexed their entire site to show over 100 + previous victims now listed as being leaked. Lockbit is the only Nastiest Malware that has consistently remained a top dog for multiple years and we expect them to keep the IT nightmares coming.
Black Basta

Black Basta is a ransomware-as-a-service (RaaS) group that was first observed in April 2022. The group spreads ransomware through phishing emails and software vulnerabilities. Black Basta may be yet another rebranding/branch of the Conti ransomware group – this seems to be a theme ever since they were fractured from the inside last year.

The group shares similar tactics, techniques, and procedures (TTPs) with other ransomware groups, like Conti and Black Matter. The group follows a double extortion approach to steal sensitive data. Black Basta looks to have stolen data from ABB, a global industrial automation company. They are indiscriminate in their targets and go after a wide range of industries, including healthcare, government, financial services, education, and media. Just like all the ransomware families on this list they will utilize botnets for the initial email into foothold infection. Then will spread laterally with white hat pen-testing tools like Cobalt Strike and to gain a foothold in the environment. Once they gain domain controller access then they’ll deploy the ransomware payload.

- “If it walks like a duck and talks like a duck then it’s probably Qakbot.”
Qakbot/Pinkslip bot/Qbot has been especially active this year.- The interesting pivot has been the usage of known good file structures and header info used in malware campaigns as well as interesting delivery mechanism.
- “Did someone order Doordash?”
- We saw delivery methods change several times this year with pivots to use OneNote files and shortcuts .lnk to deliver payloads as well as some more boutique methods.
- “They are getting smarter.”
- We saw an increase in the sophistication of phishing and malware lures likely thanks to chat GPT and similar LLMs. Even social engineering is getting better and learning about a target has never been easier.
- “It’s not safe to talk here.”
- Discord was a target with a recent disclosure of 750k users having their info leaked from a data breach. Now we’re seeing malware specifically targeting discord and discord users. What’s next?!?
Mobile Mentions
- GoatRAT: Android Banking Trojan Variant Targeting Brazilian Banks
- A new variant of the GoatRAT Android banking Trojan has been found targeting Brazilian banks that use the PIX instant payment platform.
- The malware only uses the ATS framework to carry out fraudulent money transactions and does not steal authentication codes or incoming SMS messages.
- This new variant highlights the risk of cyberattacks that do not require multiple permissions or many Banking Trojan functionalities to execute financial fraud.
- South Korean Android Banking Menace – FakeCalls
- An Android Trojan named FakeCalls has been found targeting the South Korean market.
- The malware can masquerade as one of more than 20 financial applications and imitate phone conversations with bank or financial service employees.
- FakeCalls also has the ability to extract private data from the victim's device.
- The malware developers have paid special attention to the protection of their malware, using several unique evasions techniques that have not been seen in the wild before.
- Eastern Asian Android Assault – FluHorse
- A new Android malware campaign, dubbed FluHorse, has been targeting users in Eastern Asia.
- The malware is disguised as a legitimate app and can steal financial information, contacts, and other sensitive data.
- FluHorse also has the ability to intercept and redirect SMS messages, which can be used to steal two-factor authentication codes.
- MMRAT Carries Out Bank Fraud via Fake App Stores
- A new Android banking Trojan, dubbed MMRAT, has been found carrying out bank fraud via fake app stores.
- The malware is disguised as legitimate banking apps and can steal login credentials and other sensitive information.
- MMRAT also has the ability to intercept and redirect SMS messages, which can be used to steal two-factor authentication codes.
- Android App 'Breaking Bad' Legitimate Screen Recording, File Exfiltration
- A legitimate Android app called "Breaking Bad" has been found to be secretly recording users' screens and exfiltrating the data to a remote server.
- The app is available on the Google Play Store and has been downloaded over 100,000 times.
- The app's developers claim that it is used to track users' progress in the game, but security researchers have found that it is actually collecting sensitive data such as passwords and credit card numbers.
- Android GravityRAT Goes After WhatsApp Backups
- A new Android malware, dubbed GravityRAT, has been found targeting WhatsApp backups.
- The malware can steal WhatsApp messages, contacts, and other data from the victim's device.
- GravityRAT also has the ability to steal two-factor authentication codes, which can be used to take over the victim's WhatsApp account.
- Android Apps with Spyware Installed 421 Million Times from Google Play
- A security firm has found that over 421 million Android apps have been installed from the Google Play Store that contain hidden spyware.
- The spyware can collect a variety of data from users' devices, including call logs, SMS messages, location data, and browsing history.
- The apps are disguised as legitimate apps, such as games and productivity tools.
These are just a few of the many Android malware threats that are currently circulating. It is important to be aware of these threats and to take steps to protect yourself. Some tips for protecting yourself from Android malware include:
- Only download apps from trusted sources, such as the Google Play Store.
- Be careful about what permissions you grant to apps.
- Keep your Android device up to date with the latest security patches.
- Use a security app to scan your device for malware.

Businesses
- Lock down Remote Desktop Protocols (RDP).
- Use RDP solutions that encrypt data and use multi-factor authentication. This needed increase in security protects against vulnerabilities when remoting into other machines. Make sure you are aware of all the remote desktop software being used as criminals are now installing legitimate remote desktop tools to backdoor your environments while also avoiding detection.
- Educate end users.
- Preventing attacks starts with stronger awareness among end users. Running regular cybersecurity awareness trainings and phishing simulations keeps data safe and secure. Also, make sure employees know when and how to report a suspicious message.
- Install reputable cybersecurity software.
- Choose a solution that uses real-time, global threat intelligence and machine learning to stop threats. Look for protection with multi-layered shielding to detect and prevent attacks at numerous different attack stages.
- Set up a strong backup and disaster recovery plan.
- With hybrid work with us for the long haul, businesses can’t afford to go without a strong backup. Test backups regularly and set alerts so admins can easily see if something’s amiss.
- PATCH OR DIE! 🔪💀
Individual Users
- Develop a healthy dose of suspicion toward messages.
- Treat your emails like the same way you’d treat a graveyard in a horror movie. Don’t click on links or attachments in emails. Be suspicious of any emails, texts, phone calls or social media messages that ask for personal info.
- Protect your devices with antivirus and a VPN.
- Be sure to secure not just computers, but smartphones and tablets, too. And when you ditch an old device, be sure to wipe it first.
- Keep your antivirus software and other apps up to date.
- Hackers use outdated software and operating systems to get malware onto your system and steal from you. Install updates.
- Use a secure cloud backup.
- We recommend using both an online backup that stores your data in an encrypted format and a physical backup drive that you unplug when not in use.
- Create strong, unique passwords (and don’t share them).
- Length = Strength. Use passphrases to increase the characters of passwords and defend against brute force
- You can use a password manager to help you create and store good passwords. That way, you don’t have to remember them all or write them down.
- If a file you downloaded asks you to enable macros, DON’T DO IT.
- This is a strong telltale sign that the file is infected with malicious code. Even though macros have legitimate uses, they are extremely rare in a normal home user context.
- We’ve seen some adoption of .lnk file replacements in the infection chain instead of VB Macros in an excel file. The scam is changing the icon to something that looks like a document.
Let us know what you think the is the Nastiest Malware