Our phishing series continues with an especially nefarious form, one that can be very difficult to detect once a cybercriminal has gained access to an account, likely leveraging stolen credentials, perhaps even obtained via another one of the forms of phishing we’ve covered.
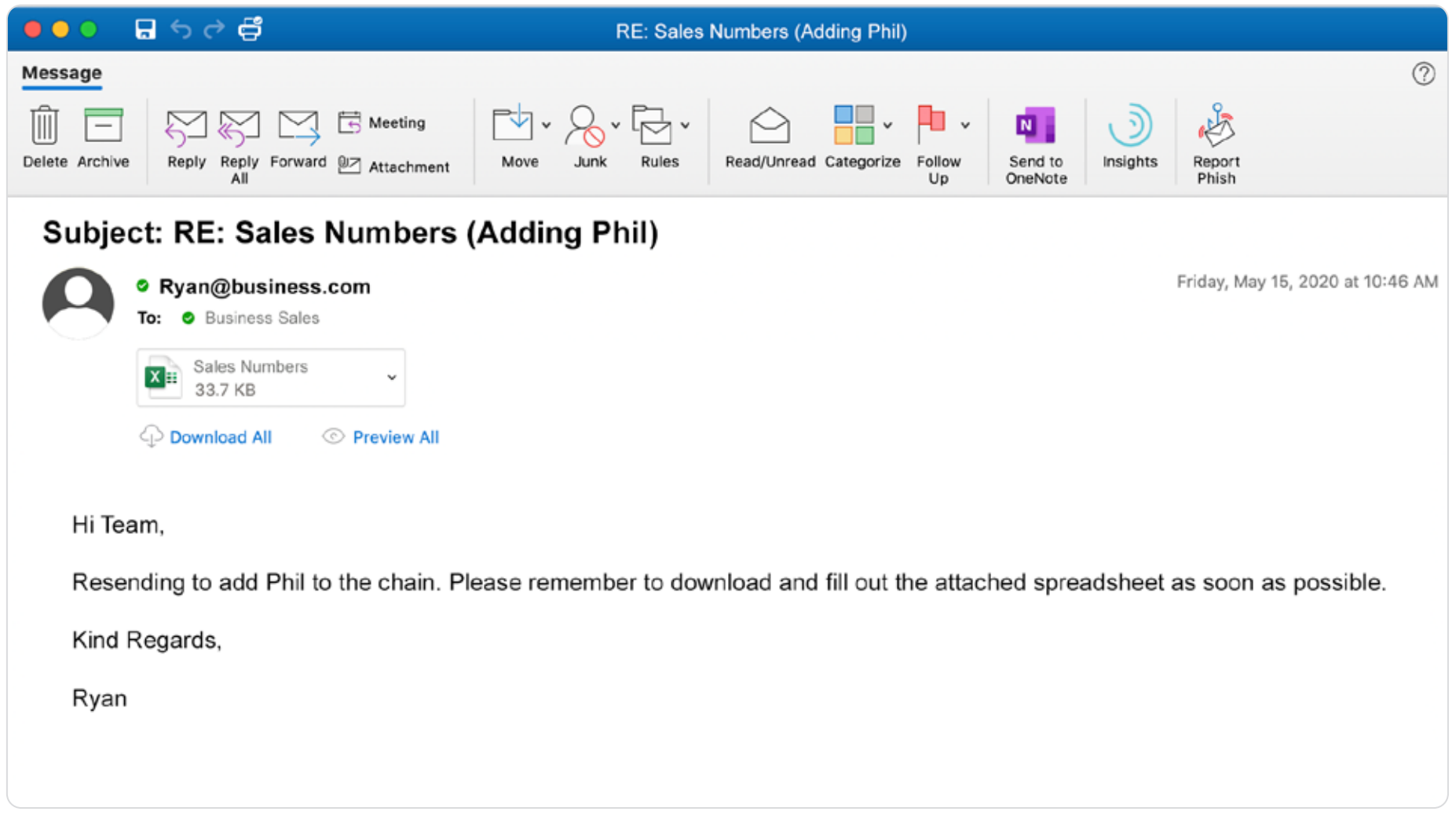
In clone phishing, a shady actor makes changes to an existing email, resulting in a nearly identical (cloned) email but with a legitimate link, attachment, or other element swapped for a malicious one. These attacks can’t get off the ground without an attacker first compromising an email account, so a good defense is using strong, unique passwords paired with two-factor authentication.
What Clone Phishing Looks Like
Download the 11 Types of Phishing eBook


