If you have any questions, please reach out and comment below!
Me
I will be talking about information theft with two other sec experts this Thursday. Register and info here:https://twitter.com/ThreatMurray/status/1105438204054962176
I will be talking more in-depth about info-theft on Wednesday next (20th March). More info and register here:
https://www.brighttalk.com/webcast/8241/348501/cybercrime-the-rise-of-information-theft-and-its-cost
Information theft
Breaches and Leaks Soared 424% in 2018
The number of different breaches and leaks has exploded in size according to a report by 4iQ. Although we are used to seeing big banner breach headlines, this swell in reported incidents is “due in part to hackers targeting larger numbers of small businesses”. The theft of data from SMEs in increasingly automated. Infections and campaigns such as Emotet, Trickbot, Gozi, Ursnif (and many others) harvest tons of sensitive data from businesses and return them to malicious actors without any kind of hacker effort.
More: https://www.infosecurity-magazine.com/news/breaches-and-leaks-soared-424-in-1?utm_source=twitterfeed&utm_medium=twitter
Iranian Hackers Stole 6TB of Sensitive Data
A coordinated and devastating attack on Citrix was attributed to Iranian hackers by infosec firm Resecurity. The goal of the attack was to steal information and over 6tb of data was exfiltrated from the enterprise giant. A lot of different tactics were used but simple password spraying (trying commonly used passwords) was one of the key tricks involved.
- “Popular enterprise software company Citrix that provides services to the U.S. military, the FBI, many U.S. corporations, and various U.S. government agencies disclosed last weekend a massive data breach of its internal network by "international cyber criminals."
- “However, the FBI believes that the miscreants likely used a "password spraying" attack where the attackers guessed weak passwords to gain an early foothold in the company's network in order to launch more extensive attacks.”
- "Based our recent analysis, the threat actors leveraged a combination of tools, techniques and procedures (TTPs) allowing them to conduct targeted network intrusion to access at least 6 terabytes of sensitive data stored in the Citrix enterprise network, including e-mail correspondence, files in network shares and other services used for project management and procurement."
809 million records exposed by email marketing giant
More: https://securitydiscovery.com/800-million-emails-leaked-online-by-email-verification-service/STOP Ransomware Installing Password Stealing Trojans on Victims
The different categories of infections are getting increasingly blurred. Malware dropping other completely different types of malware is commonplace now. Back in January we witnessed Emotet (modular malware) dropping Trickbot (banking trojan) which then led to Ryuk (ransomware) being dropped on a single environment.
The news that Stop ransomware is now installing an Azorult password stealer on machines shouldn’t be too surprising. Admins should see any serious malware breach as a potential tip-of-the-iceberg scenario and get in contact with their AV support to try to find an attack vector.
More: https://www.bleepingcomputer.com/news/security/stop-ransomware-installing-password-stealing-trojans-on-victims/
“Tech security at Equifax was so diabolical, senators want to pass US laws making its incompetence illegal”
Sometimes a breach is so bad it sparks an investigation and leads to changes in legislation. The Equifax breach was really bad and that’s exactly what has happened since it was revealed in 2017.
- “Credit-rating monitor Equifax ignored years of warnings and red flags before it was thoroughly ransacked in 2017 by hackers, who made off with the personal information of roughly 150 million Americans, Brits, and Canadians, according to another congressional probe.”
- “An investigation [pdf] by the US Senate Committee on Homeland Security and Governmental Affairs found that the credit agency was negligent in both the periods before and after it was hacked. The publication of the committee's findings this week follows a similarly scathing report issued late last year by House reps.”
- “According to the Senate panel, Equifax staff knew their systems were not tightly secured and open to attack in 2015, yet failed to properly secure their networks, and were eventually pwned two years later via a hole in an Apache Struts 2 installation – a security hole that a patch was publicly available for but had not been deployed.”
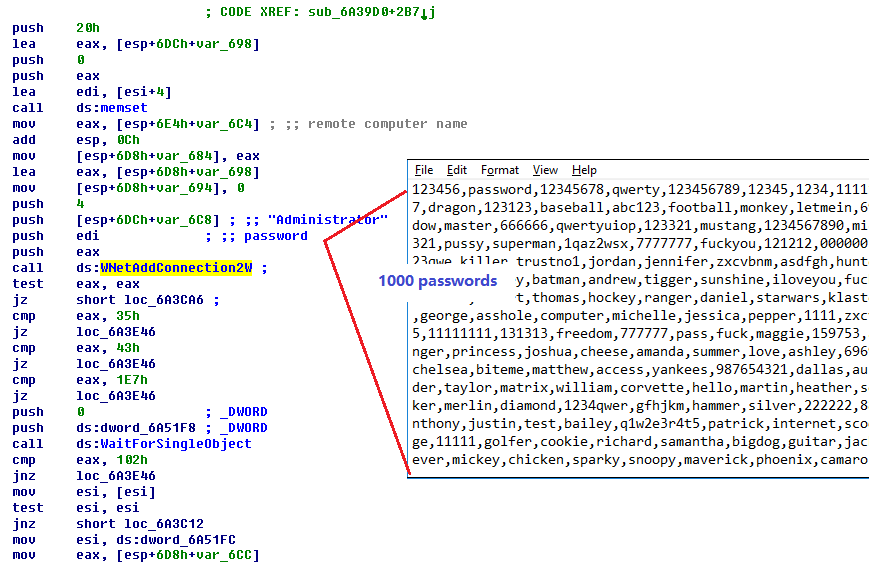
Geeky Emotet Analysis
Excellent deep-dive on Emotet’s latest features from Fortinet. Lot of techy file analysis detail here but certain features (like trying the top 1000 passwords when trying to break accounts) proves that the simplest tricks are the best:
Ninja MSP checklist
Here is a great little guide published recently by Ninja RMM. It contains a concise but comprehensive checklist to secure your MSP:More: https://go.ninjarmm.com/msp-cyber-security-checklist-2019-download-eu/
Thanks,
Kelvin